Fortinet Addresses Multiple Critical and High-Risk Flaws

This month, Fortinet released a significant security update that addressed multiple vulnerabilities. This addresses issues across its product portfolio, including FortiOS, FortiProxy, FortiManager, and FortiAnalyzer.
Such disclosures are not uncommon. However, they pose a challenge to network and security professionals striving to secure their networks. Already overwhelmed, news of new vulnerabilities might not even cut through the noise of a busy admin’s life, let alone be something they have time to address. 92% say more network updates are needed than they can keep up with.
This is where BackBox’s network vulnerability intelligence capabilities can help. With BackBox, you can:
- Easily keep TRACK of vulnerabilities
- Understand if they’re RELEVANT to your specific network inventory
- Determine the bigger context of CRITICALITY with a risk scoring of each vulnerability and device
- Quickly and easily CLOSE THE LOOP between identification and remediation
Tracking Vulnerabilities
Understanding CVEs is essential, but they don’t provide the context to make decisions. Are two critical CVEs equal? BackBox provides a vulnerability and threat feed that includes CVE information and additional context about the vulnerabilities concerning the affected devices. This is crucial. Many vendors take the list of CVEs from the National Vulnerability Database and present it in an easily digestible format. That isn’t sufficient.
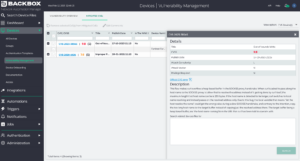
BackBox gives you external context along with the CVEs. Is the vulnerability known to be exploited? What’s the impact of an exploit? How easy is it to be exploited? All of this information is important beyond a simple list of CVEs. Vulnerabilities can be viewed by device, seeing all the vulnerabilities on the device, or by vulnerability, and seeing all the devices impacted. The following screenshot shows the list of CVEs, with relevant devices highlighted for one.
![]()
Relevant Vulnerabilities
Using search, you can determine if a vulnerability is relevant. For example, let’s say a device vendor released CVEs on http server vulnerabilities. BackBox users would quickly search all their configs for that vendor to see if the http server was set to determine if it was relevant. BackBox could quickly release an automation to mitigate this vulnerability by turning off the http server and http secure server, so customers who could turn those features off could do so quickly and easily at scale.
Vulnerabilities that are not relevant can be marked with notes indicating their irrelevance, allowing them to be set aside. Marking a vulnerability as mitigated or irrelevant removes it from the risk score measurement we will discuss next.
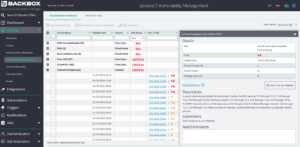
Vulnerability Criticality
Once again, it’s about a list of CVEs and comprehending the context of vulnerabilities concerning the user’s network inventory. BackBox achieves this by assigning a risk score to each CVE and device. This risk score indicates the vulnerability’s impact on the network by considering, for instance, the number of CVEs on a device, the ease of exploitation, whether they are known to be exploited, the severity of the exploit, and so on.
In summary, BackBox helps track vulnerabilities, determine which ones are relevant, and then, among those relevant, assists in understanding the potential severity of the vulnerabilities. By using this information about severity (or criticality), you can prioritize remediation.
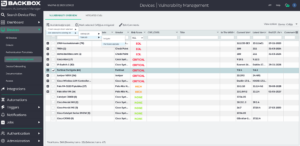
Closed-Loop Remediation
Network and security professionals already have more than they can do, even without dropping everything to patch vulnerabilities when they randomly pop up without concern for our existing workloads. BackBox closes the loop between vulnerability tracking, scoring, and remediation and automates remediation so that identified vulnerabilities are fixed with as little effort as possible. Similarly, if mitigation is necessary, BackBox provides the search and automations required to determine where a CVE is relevant and automate the actions to mitigate the vulnerability.
The following image illustrates how a Fortinet Fortigate is integrated into an update automation process to eliminate vulnerabilities.
Conclusion
You can’t control the inputs – vulnerability notices from vendors – but you can control your response. Are you able to respond quickly? Can you triage vulnerabilities swiftly to assess their severity and impact? Can you easily and quickly mitigate vulnerabilities? These are the questions you must consider; otherwise, you’re doing your organization a disservice. No matter how busy we all are, keeping our networks safe is essential.
BackBox vulnerability intelligence enables network and security teams to save time, reduce errors, and manage the vulnerability lifecycle proactively. Our platform identifies and correlates known vulnerabilities with your inventory of network and security devices. It prioritizes these vulnerabilities based on their risk and your security posture while offering options to automate updates or implement configuration workarounds.
Discover the advantages of BackBox today. Schedule a 30-minute demo for an interactive tour of the BackBox platform.


