BackBox Features
Get secure, powerful, scalable automation for your modern network infrastructure
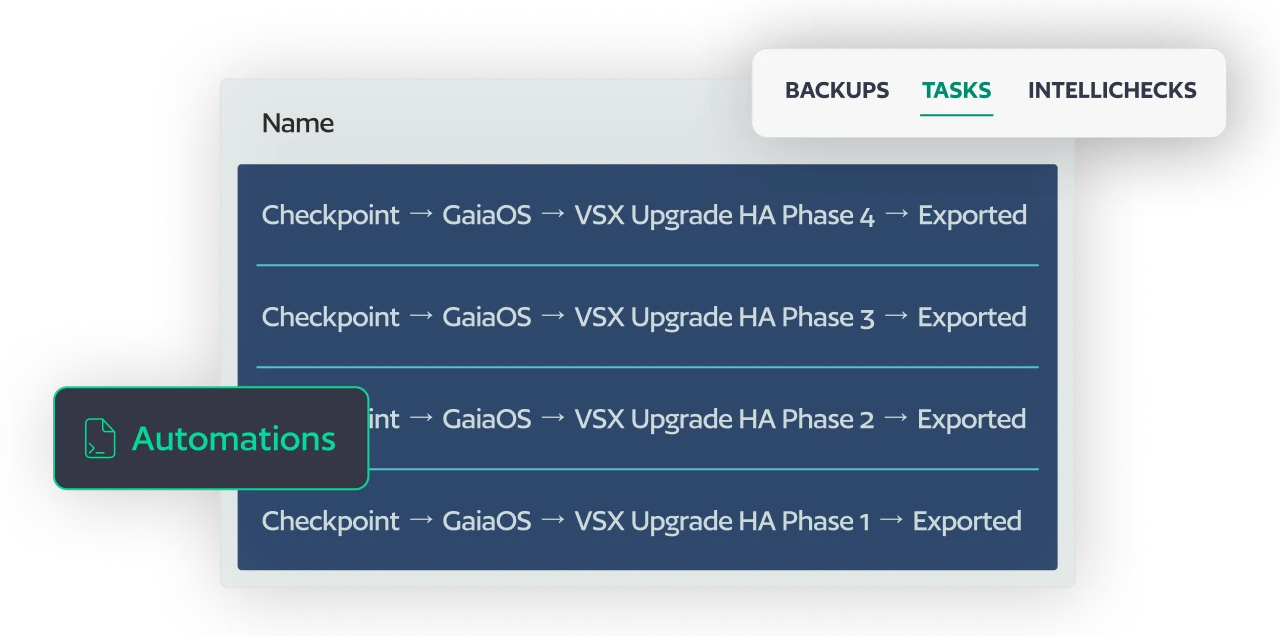
Automated Lifecycle Management
- Onboarding
- Device Inventory
- Backup & 1-Click Restore
- Automated OS & Firmware Upgrades
- Lifecycle Management
Compliance & Policy Management
- Contextual Automation
- Change Auditing
- Reporting
- Automated Compliance and Remediation
- Role Based Access Control
Network Infrastructure Integrity
- Discovery & Mapping
- Risk Scoring
- Vulnerability Remediation
- Change Monitoring
- Access Management
Over 100,000 networks worldwide choose BackBox

Get the Buyer’s Guide
Identify critical factors to consider when choosing a network cyber resilience platform.
Automated Lifecycle Management
Back up, validate, and restore all your devices with a single click.
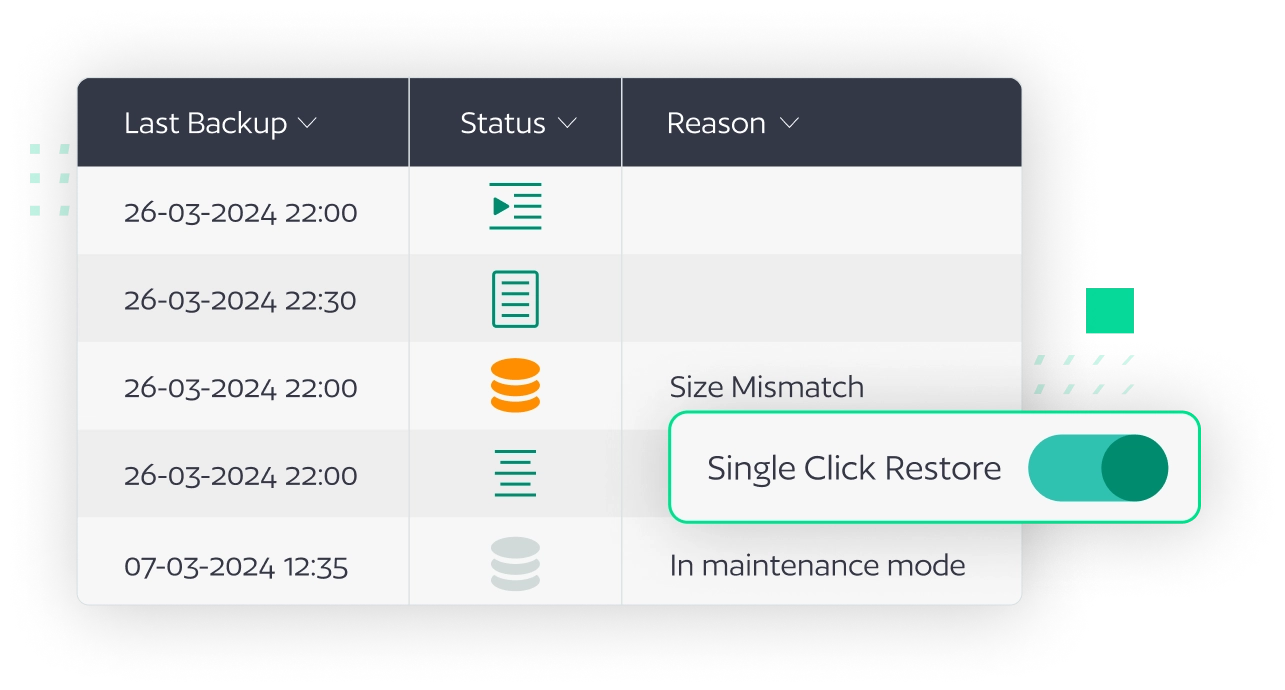
Onboarding
BackBox enables greenfield and brownfield provisioning by adding devices through IP range, CIDR block, or CSV import. When new devices are brought into the network, tasks are automated to match the config policy.
Device Inventory
BackBox automates the collection of details about your network devices, gathering and organizing helpful information such as device models, hostnames, specific OS versions, CPU type, total RAM, and more.
Automated OS & Firmware Upgrades
BackBox features comprehensive upgrade automations, including multi-step and high-availability aware upgrades. You can chain pre- and post-check automations to automate upgrade testing within your process.
Lifecycle Management
BackBox equips you with vital end-of-life insights, empowering you to easily plan and execute hardware replacements and upgrades. Don’t leave your technology to chance—strategize effectively and keep your systems running smoothly.
Backup & 1-Click Restore
BackBox ensures success by thoroughly validating all backups. With just one click, you can restore device configurations and operating systems with one click, even to bare metal for replacing devices.
Compliance & Policy Management
Run compliance checks on devices to assess resilience.
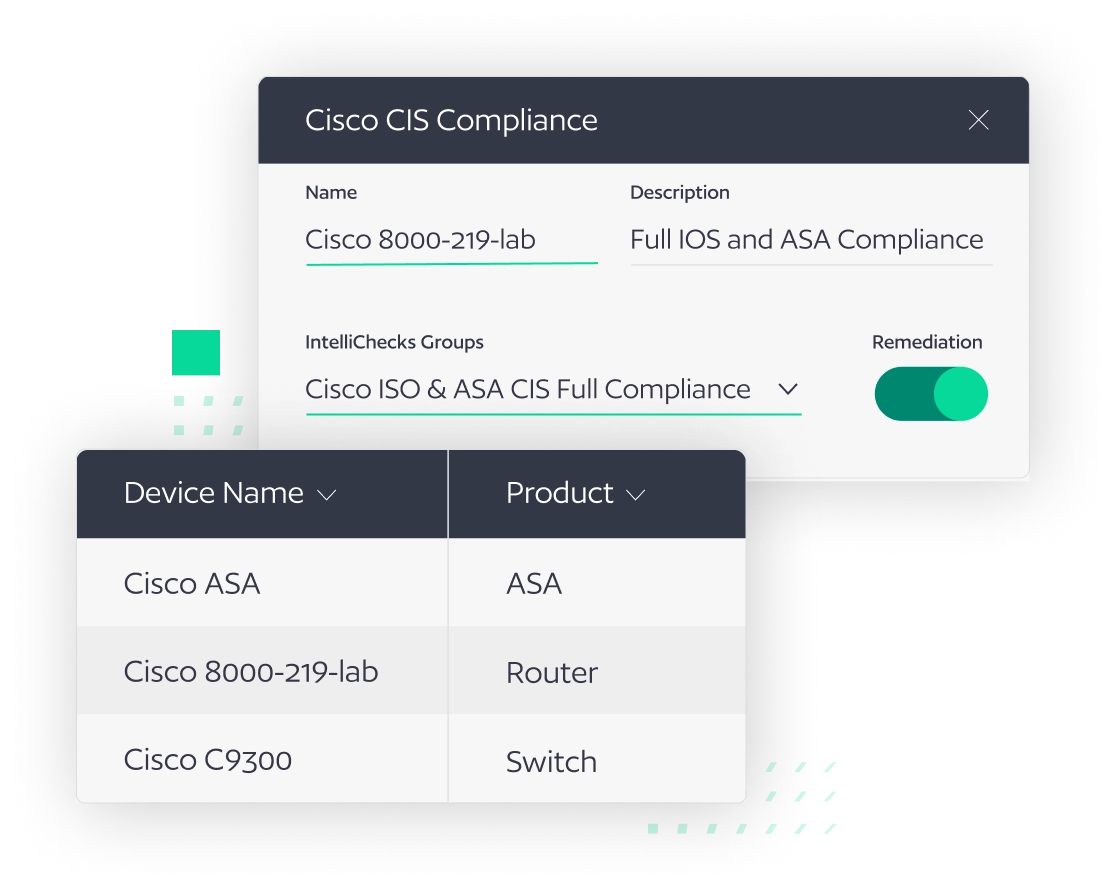
Contextual Automation
IntelliChecks, BackBox’s contextual automations, makes available a large set of functionality with 1500+ advanced automations built into the product with advanced features, including compliance auditing, remediation, technical survey, and reporting.
Role Based Access Control
BackBox offers flexible role-to-privilege mapping and integrates with password vaults and SSO solutions, simplifying security and administration across sites and enabling secure and auditable delegation of network tasks.
Reporting
Inform decision-making by running automations that generate customized reports for your diverse environment and processes.
Change Auditing
BackBox Compare Tool makes comparing configuration baseline parameters, compliance expectations, or any other files easy.
Automated Compliance & Remediation
With a built-in library of compliance and remediation automations, BackBox delivers a simple way to baseline and scale compliance activities such as DISA STIGs, CIS Benchmarks, DORA, and more.
Network Infrastructure Integrity
Proactively identify active exposures you are vulnerable to.
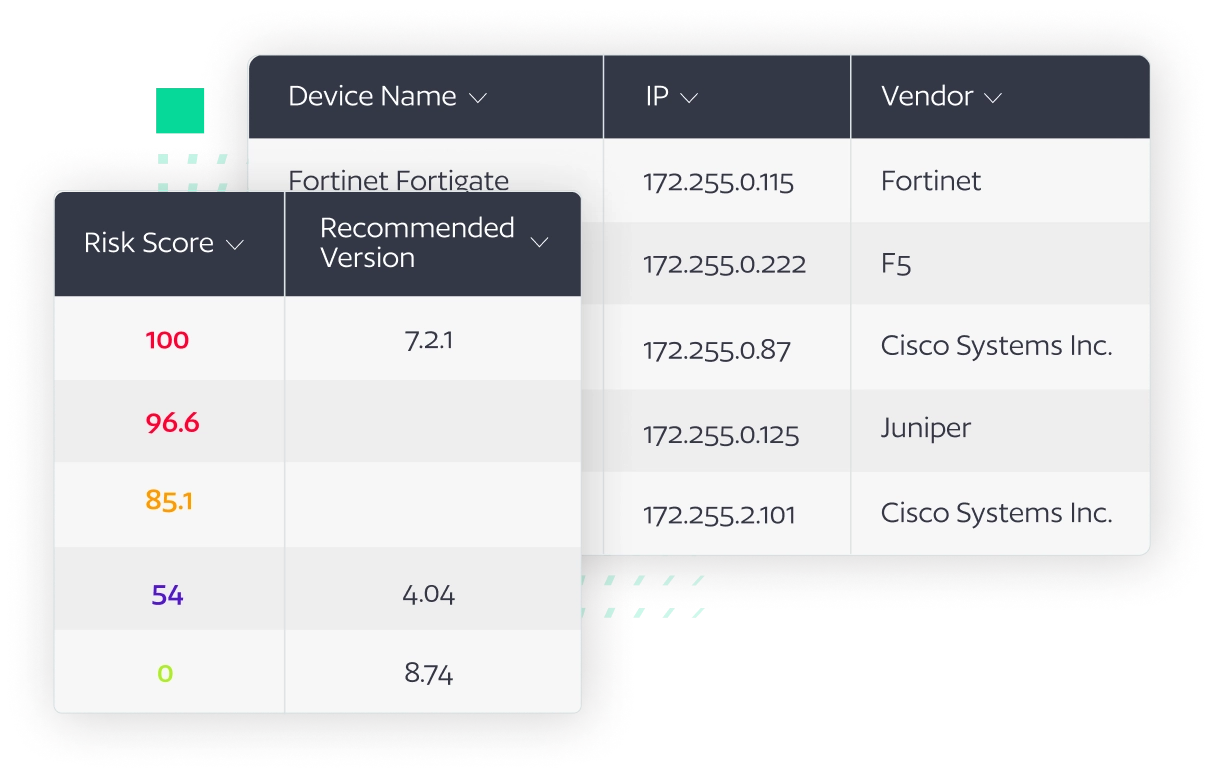
Discovery & Mapping
BackBox models your network's configuration inventory, which is mapped against a threat and vulnerability intelligence feed that uses CVEs and other security information to determine the threat level against your specific inventory.
Risk Scoring
Risk level, recommended updates and patches, and product end-of-life information provide recommended automations to remediate discovered vulnerabilities and help you prioritize device patching based on actual risk to their network.
Vulnerability Remediation
Easily discover vulnerabilities in your network, prioritize CVEs according to their unique risk profile, and take remediation action, regardless of network complexity.
Change
Monitoring
Run vulnerability reports based on device inventory to understand risk and security posture and prioritize efforts and resources appropriately.
Access Management
Record terminal sessions to easily audit and review access history (and utilize for compliance and training purposes), ensuring commands are completed while providing status notifications.
We’re here for you
Proactively identify active exposures you are vulnerable to.
World-Class Support
Our support organization boasts an NPS of over 90, making it the best. BackBox Automation Labs, the brains behind the Automation Library, collaborates with customers to create tailored network automations.
Flexible Deployment Models
BackBox can be deployed on-prem or public/private cloud, giving customers and service providers the maximum deployment flexibility.
Distributed Architecture
BackBox has a distributed architecture designed for scalability and performance, using an agent-based model for low-bandwidth sites. It supports high availability with a hot backup server for fault tolerance and automates security and network devices, enhancing local control over automations and files.
REST API
BackBox is built with an API-first philosophy. Our REST API enables powerful custom bidirectional integrations, and external applications can interact with BackBox automations through the API.

Protect Your Network from Vulnerabilities and Disruptions
Our Recent Awards
Want to see BackBox in action?
Contact us to schedule a demo and discuss what your organization can do with BackBox



