BackBox Introduces Network Vulnerability Manager
NOTE: Originally published on November 15, 2023. Network Vulnerability Manager is now called Network Vulnerability Intelligence. The post below was updated on March 26, 2025, to reflect this.
The BackBox network cyber resilience platform helps network superheroes track and remediate network and security device vulnerabilities (CVEs and more) in a way especially designed for IT and security teams.
BackBox provides administrators with the necessary tools to safeguard their networks by integrating device inventory with a vulnerability intelligence feed. Correlating threat and vulnerability intelligence with precise network inventory enables risk scoring, allowing administrators to identify their most vulnerable areas. Gartner refers to this approach as “evidence-based security.”
Through 2026, more than 60% of threat detection, investigation, and response (TDIR) capabilities will leverage exposure management data to validate and prioritize detected threats, up from less than 5% today. (Gartner, December ’22)
Building our vulnerability intelligence capabilities on a network automation platform means we identify your vulnerabilities and automate the fix to protect you.
Administrators can step away from their email, put down their spreadsheet trackers, and trust that the CVE and vulnerability information they see in BackBox relates to their network.
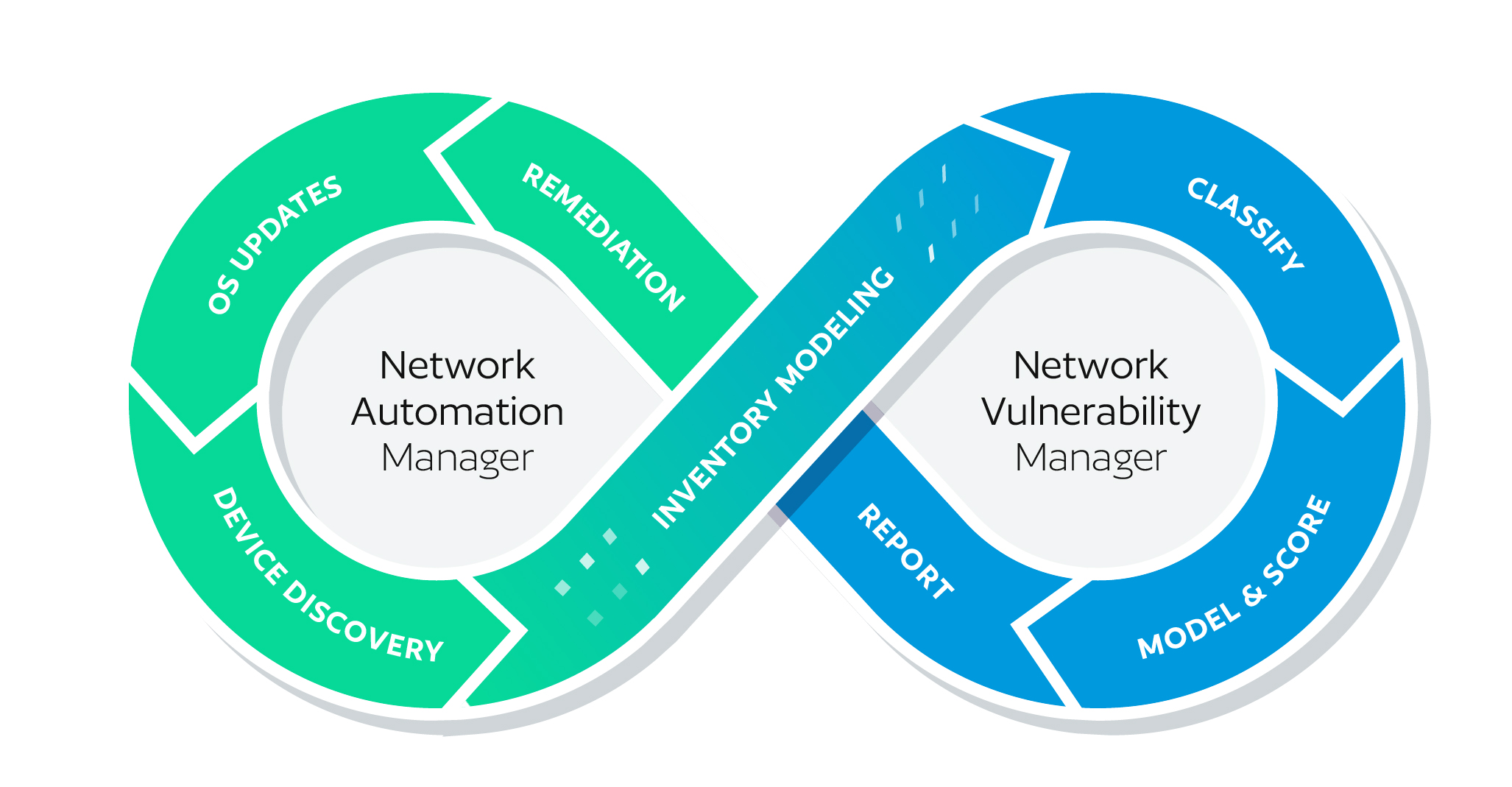
The Closed Loop
There are three key elements in BackBox’s closed-loop remediation of vulnerabilities:
- Dynamic device inventory – inventory that’s kept up to date automatically.
- Device modeling and risk scoring – a threat and vulnerability intelligence database that’s updated automatically.
- Remediation – taking inventory of vulnerabilities and automating vulnerability patches to keep networks secure.
Dynamic Device Inventory
BackBox includes an automation job for collecting inventory. Each time this job is run, the inventory is updated to reflect any additions, moves, and changes in the network since the last inventory.
This means that your actual network inventory is used and that the CVEs and other vulnerability risks presented relate exactly to your network. You’re not wasting time chasing down security alerts that aren’t relevant to your inventory.
Any remediation done is automatically reflected in the next inventory and propagated to BackBox due to minimizing manual tracking (and the potential for manual errors).
Device Modeling and Risk Scoring
CVEs and other vulnerability intelligence are collected, normalized, and modeled to be consistently applied against the inventory collected in the previous step.
Other solutions use the NIST NVD to gather CVE information and incorporate it into their products. This can be useful, though not necessarily complete. With BackBox, we ingest CVEs and other critical information from CISA, vendor websites, and more. We score this information to help you understand your network’s actual vulnerability state.
Gartner suggests that security and risk management leaders responsible for vulnerability management apply quantification principles to allow for vulnerability management prioritization (Gartner subscription required). That’s what the vulnerability intelligence capabilities in BackBox do for network security administration.
Risk scoring provides a method for quantifying the vulnerability state while modeling the information, which helps us understand when vulnerabilities apply to a specific configuration.
Remediation
Most vulnerability management systems are informational only. They tell you where you might be exposed, but they cannot do anything with the information presented—until now.
Because our vulnerability intelligence capabilities are built on our platform, we can remediate the fix and inform. And, with the BackBox approach to automation—where our Automation Library has over 3,000 automations built-in—we have the breadth of expertise to automate the OS updates or configuration changes required to patch known vulnerabilities.
Implementation
BackBox makes it easier to tackle OS Updates and vulnerability patching.
Simple to Get Started
A prebuilt automation job collects all the information you need to pass to the vulnerability intelligence engine. This engine does all the “hard work,” taking the dynamic inventory and mapping it against the vulnerability database to determine risk scoring and relevance. The mapping work is done behind the scenes and doesn’t require user manual intervention.
The job is in the Jobs menu under the ‘vulnerability intelligence’ tab. Create a new Vulnerability Intelligence job by hitting the ‘+’ and filling out the required fields. When you hit save, you’ll be given the option to select what information to share. Once the job is configured, run the job and see your vulnerability state.
Simple to Use
Using our vulnerability intelligence capabilities is simple, too. Under the Devices menu item, you’ll see a tab called “Vulnerability Intelligence.” If you’ve already run the job to collect inventory, your inventory will appear in this tab.
This tab lists your devices with risk scoring, CVE information, recommended updates, and, if available, product end-of-life information. Devices can be added to remediation jobs directly from this tab to mitigate vulnerabilities.
No Scripting Required
As with all the other automations in BackBox, no scripting is required. If you have external scripts you want to leverage, you can, but you don’t have to script anything to use BackBox.
If the automation you need is unavailable, you can easily modify an existing one or create what you need from scratch. You only need the commands (API or CLI) you want to run, and BackBox does the rest.
Why does this matter? Regarding upgrades, you may have custom test scripts that you want to run as pre- or post-checks. You can easily do this as part of the remediation sequences.
Device Lifecycle Management
BackBox also includes end-of-life (EOL) data, where available, to help administrators manage the hardware replacement lifecycle.
This EOL information is essential since vulnerabilities are present in devices that no longer receive OS updates. This means that devices that are vulnerable need configuration changes to patch them, if that’s even possible. And the only way to shut down vulnerabilities on these devices if their configurations can’t be patched is to replace the hardware.
Seeing is Believing
Whether you’re a customer or not, we’d love for you to try out this new capability and see how simple yet powerful a tool it can be for keeping your networks secure. If you’re a customer, upgrade to version 7.5, look for the Vulnerability Intelligence tab under devices, and click Contact Support.


