Set Your Network Vulnerability Intelligence Program on the Right Course

Vulnerability intelligence is crucial for maintaining network security. As networks become increasingly complex, vulnerabilities rise, placing pressure on teams to identify and resolve these issues. There are two steps every network and security team should take to enhance their network security posture:
- Mitigate defined cybersecurity threats via programs that reduce an enterprise’s exposure to associated exploits and threat vectors.
- Leverage threat intelligence and research to identify relevant threats emerging from the cloud of uncertainty swiftly. It’s crucial to monitor inventory and security alerts daily and combine them to reveal actionable threat and vulnerability information. Avoid focusing on the probabilities of exploits; seek specific details about exploits in your network configuration.
The goal is to leverage your knowledge to enhance your network’s security rather than attempt to predict the uncertain future. By utilizing network vulnerability intelligence solutions, network and security teams can swiftly identify the vulnerabilities affecting their networks, assess their significance, and determine the necessary actions to mitigate or resolve them. Maintaining this approach at the core of your network vulnerability intelligence program will help ensure its effectiveness.
Benefits of a Network Vulnerability Intelligence Program
Vulnerability intelligence aids enterprises in pinpointing and proactively addressing potential security vulnerabilities, preventing them from evolving into significant cybersecurity threats. This proactive approach safeguards against security breaches and protects a company’s reputation and financial standing.
Practical vulnerability intelligence improves compliance with protocols and regulations. Additionally, it gives organizations a clearer understanding of their overall security risk landscape and identifies areas where enhancements can significantly affect their security posture.
In today’s interconnected landscape, relying solely on sporadic security scans and reacting to cyber threats is inadequate as a cybersecurity strategy. Network vulnerability intelligence offers three key benefits:
- Improved security. Often, vulnerability tracking is done in a spreadsheet without understanding the exact network inventory you’re protecting. An automated network vulnerability solution helps map your exact inventory against known vulnerabilities to help visualize your security posture and gamify improvements. BackBox also automatically analyzes new devices onboarded to ensure that no new known vulnerabilities are added to the network as they’re connected.
- Reporting and collaboration. Security is a team sport, yet security teams are increasingly overwhelmed by the growing attack surface they must address to protect their organization from rising attacks. Network teams can help. With a network vulnerability management tool that allows them to report on vulnerabilities and necessary remediation activities for devices within their scope of responsibility, network teams can proactively keep their peers in security and compliance up-to-date and help alleviate the burden they face.
- Operational efficiency. Device updates are complex, time-consuming activities. Prioritizing and simplifying them based on their impact on security is critical in improving the network team’s effectiveness against threats and strengthening the organization’s overall security posture.
Steps of the Network Vulnerability Intelligence Process
1. Track vulnerabilities
The vulnerability intelligence process starts with collecting and mapping the network inventory against the vulnerability feed. Network inventory is collected automatically by a solution like BackBox, so we know exactly what vendors, devices, and versions are on the network.
A vulnerability feed is a stream of information about vulnerabilities. It is often a list of CVEs, but that’s not enough. BackBox also incorporates CVEs from the National Vulnerability Database and enriches that information with context from elsewhere, such as CISA, vendor information feeds, etc. An enriched feed effectively tracks vulnerabilities and their status — are they being exploited? What’s the potential for harm? How easy is it to exploit them?
Mapping the inventory against the vulnerability feed is the first step in the network vulnerability intelligence process.
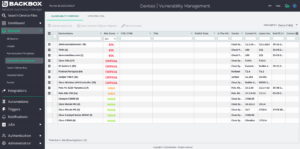
2. Score the devices
Using this feed and the inventory in your network, devices and networks are scored to assess their vulnerability status. This score, which considers the number of CVEs, their criticality, and other metadata, allows network engineers to classify certain CVEs as irrelevant or for later review. This enables them to prioritize remediation and mitigation efforts on those with the most significant potential impact on the organization.
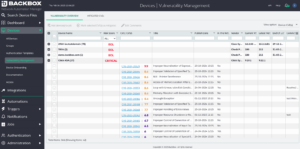
3. Mitigate or remediate
Sometimes, vendors include mitigation instructions in their CVEs, but mitigation is often left to remediation via a software update. In either case, BackBox provides automations to simplify the process.
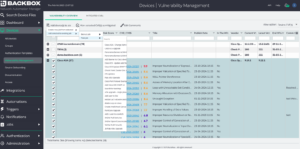
Summary
BackBox vulnerability intelligence helps network and security teams save time, reduce errors, and proactively manage the vulnerability lifecycle. Our platform identifies and correlates known vulnerabilities with your inventory of network and security devices. It prioritizes these vulnerabilities based on their risk and your security posture and offers options to automate updates or implement configuration workarounds.
Discover the advantages of BackBox today. Schedule a 30-minute demo for an interactive tour of the BackBox platform.


