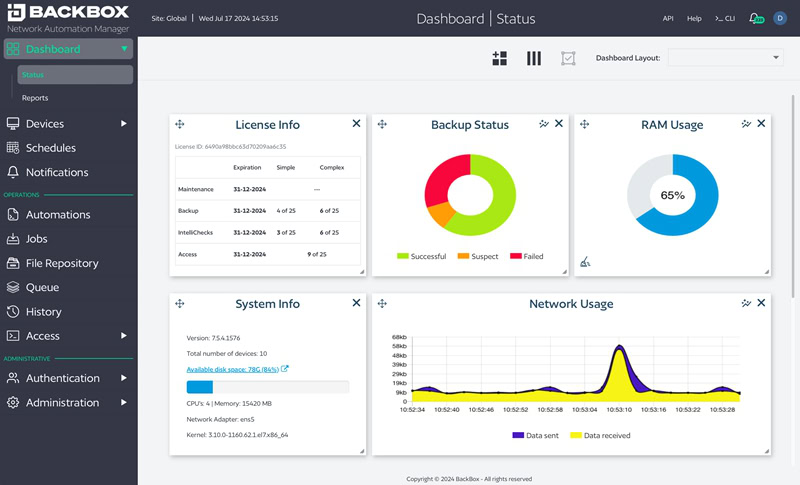
Threat Exposure vs Risk Management
Why risk management? Risk and risk mitigation involve predicting future probabilities and investing to minimize the likelihood of a breach. Predicting the future is a fool’s game with uncertain and unknowable outcomes. Risk modeling, they say, becomes security theater. Risk Assessment has transformed into a tool for persuasion—essentially, “security theater”— instead of serving as a […]