BackBox Platform
What’s New in BackBox
Our latest release offers a unified view of your modern network infrastructure, enabling the automation of network security, compliance, and lifecycle management.
Request a Demo
Experience the latest release of BackBox below and check out the release notes for deeper insights into the available capabilities.

Gain a Holistic View of Network Cyber Resilience
Our new Platform Home Page provides a comprehensive view of cyber resilience, allowing users to quickly evaluate their network’s adherence to best practices and security policies, thereby ensuring the network remains resilient against threats.
Easily Manage Devices Across Diverse Modern Networks
BackBox offers lifecycle state management for network devices, allowing teams to effectively onboard, promote, and manage them. The lifecycle states — Staging, Active, Maintenance, Ignored, and Orphaned — are available in device metadata, supporting automation and compliance checks. This ensures efficient tracking and management of devices for security, compliance, and operational integrity.

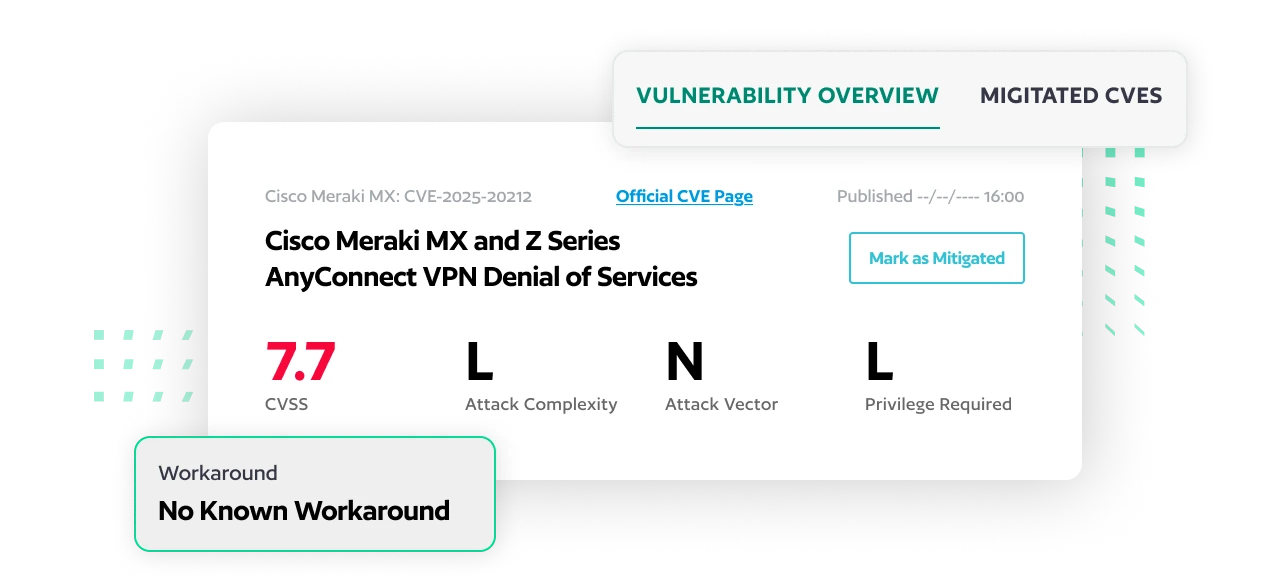
Achieve Visibility and Compliance for Cisco Meraki Devices
Ensuring compliance before deploying cloud-managed/SASE devices is tough. Non-compliant configurations can create security risks and operational issues. BackBox automates the import of Meraki devices into a staging environment, validating compliance, detecting orphaned devices, and identifying vulnerabilities while offering workaround or mitigation guidance on configurations.
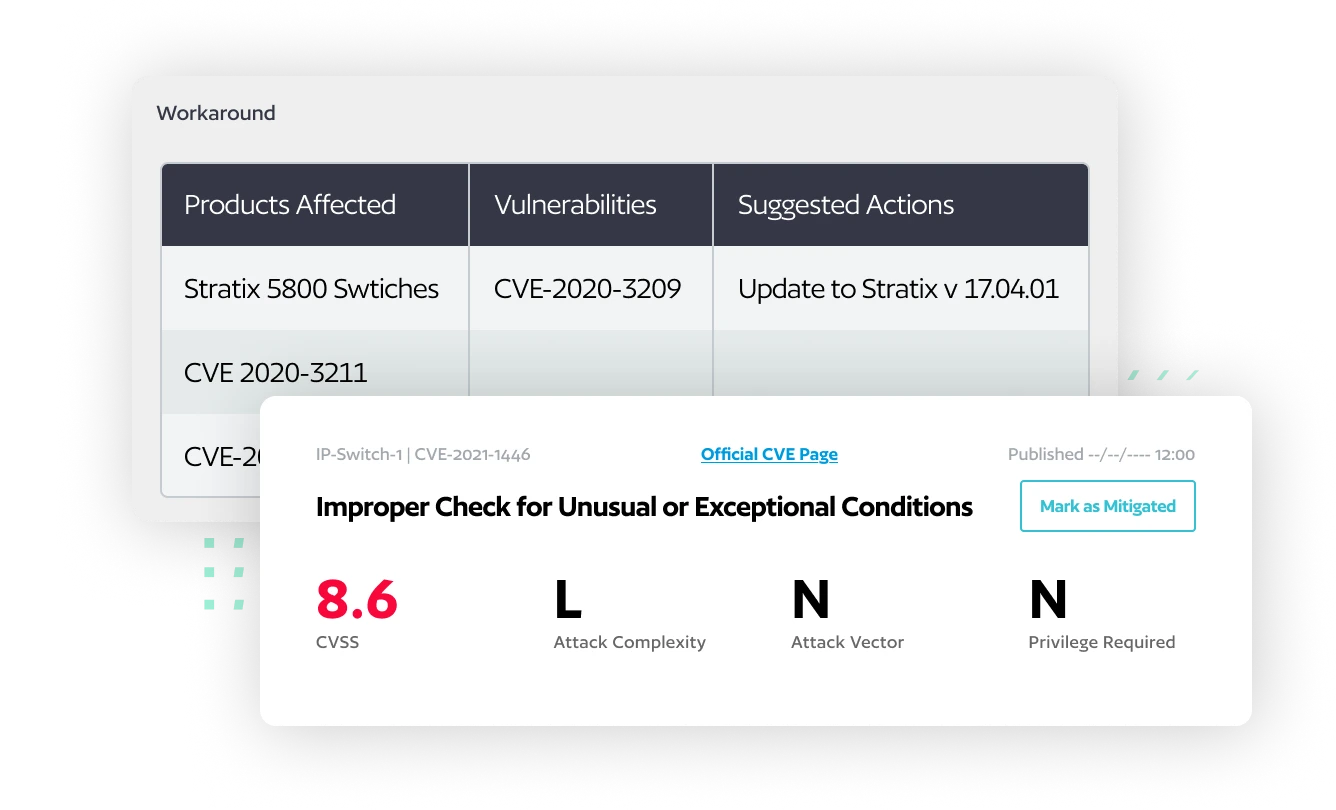
Identify Which CVEs Have Available Workarounds
Reduce your attack surface by implementing a workaround without requiring patches or upgrades, which allows network operations to continue. We’ve enhanced our vulnerability intelligence capabilities, enabling users to identify which CVEs have available workarounds to address vulnerabilities through configuration changes, saving valuable time compared to full device upgrades.

Easily Track Configuration and Inventory Changes
Tracking network device configuration and inventory changes for compliance, such as DORA, can be challenging. The latest release allows users to generate and compare reports between two dates, offering filtered options to monitor changes, ensure compliance, and streamline audits.
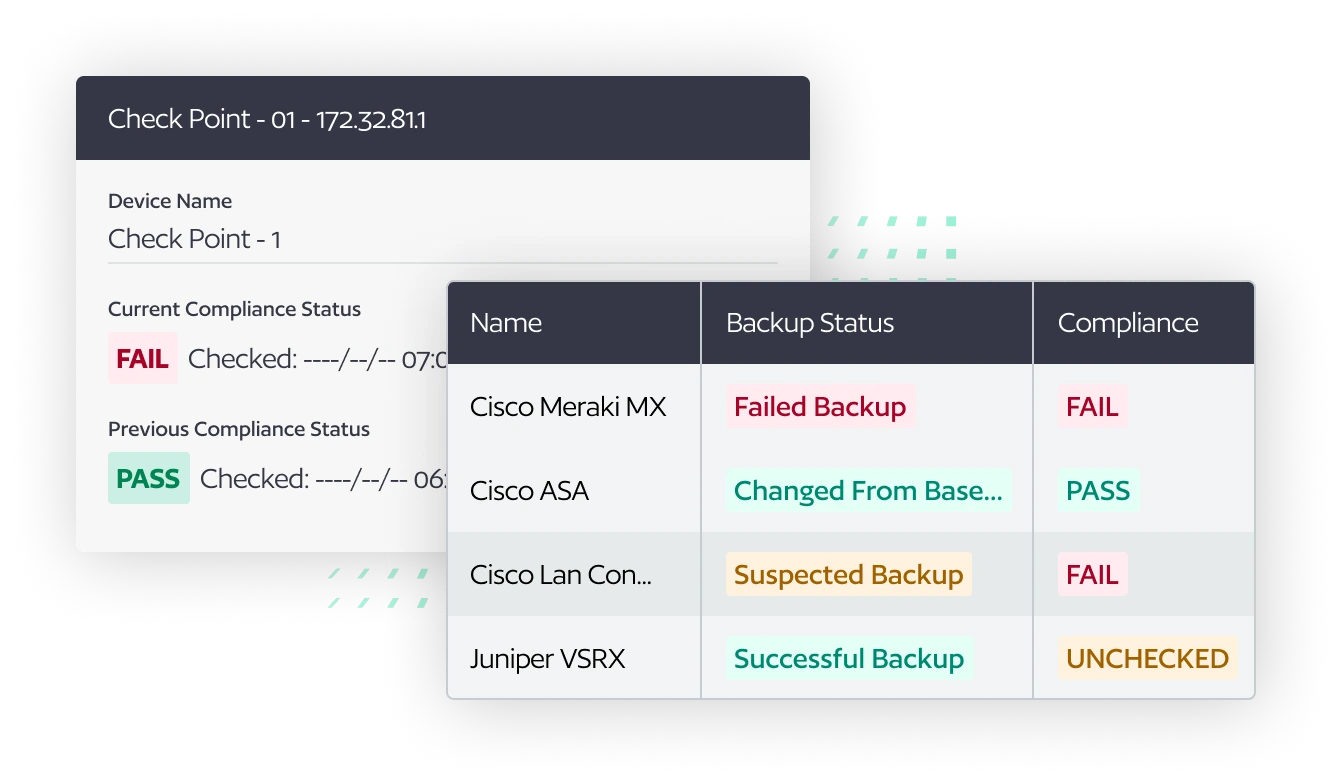
Quickly Verify Device Compliance
Network teams often lack visibility into device-level compliance, resulting in security gaps and audit failures. BackBox now provides a Compliance Status for each network device, indicating whether it is Unchecked, Pass, or Fail based on compliance standards to find and fix non-compliant devices before they become security vulnerabilities.

Hardening Agent to Server Communication
With the deployment of BackBox servers and agents, users can now choose the direction of agent communication. Agents can securely initiate communication with the management server to check for new messages and tasks. This eliminates the need for inbound HTTP connections, enhancing security and simplifying network configuration.
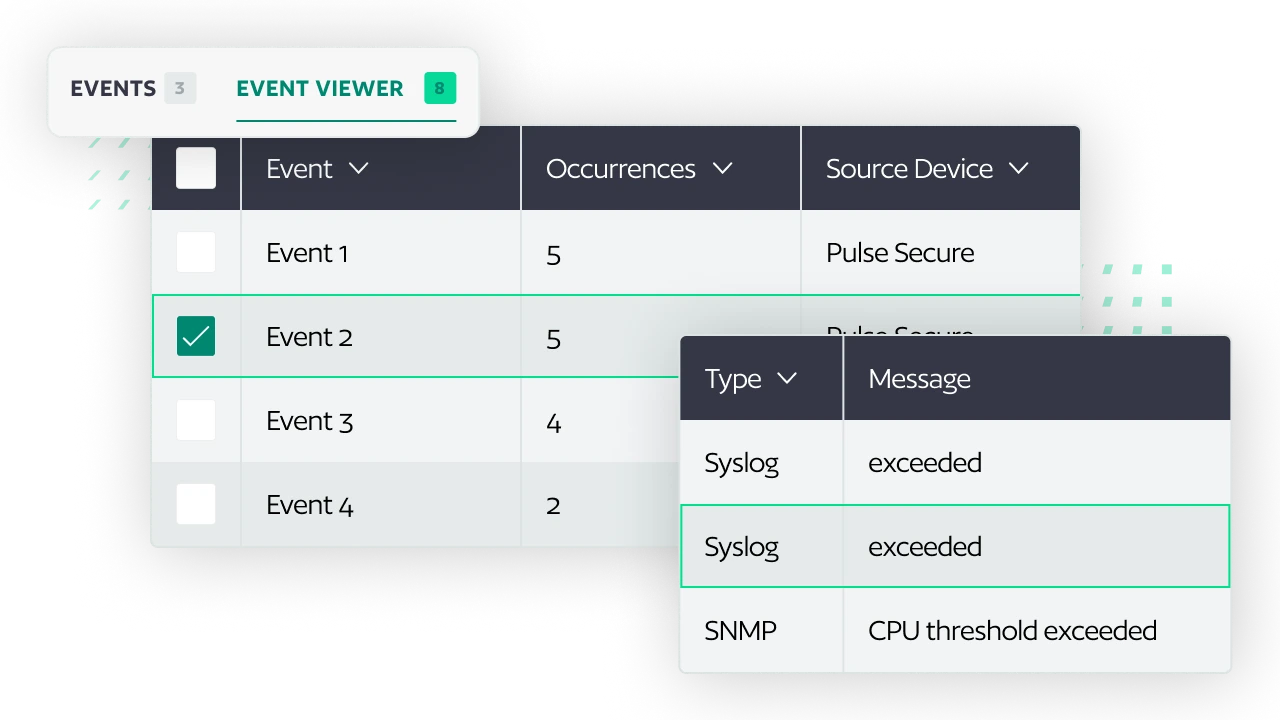
Understand Event Patterns Before Deployment
As network environments grow more complex, gaining visibility is crucial for decision-making. Our enhanced event driven automation now includes the Event Viewer, allowing users to search, filter and review event messages received from source devices. Understanding event patterns before deployment ensures accurate and predictable automation behavior.
“Every day, dedicated network and security professionals assist our team at BackBox in enhancing network cyber resilience, resulting in remarkable achievements. By collaborating closely with our customers, we have seen the impressive results that BackBox 8.0 provides, helping customers gain visibility, demonstrate compliance, and protect their networks — both on-prem and cloud-managed environments.”

Richard Phillips
VP of Technology and Infrastructure, BackBox
Want to see BackBox in action?
Contact us to schedule a demo and discuss what your organization can do with BackBox