Why BackBox
Setting the Standard for Securing Modern Networks
In a landscape filled with point solutions, our network cyber resilience platform stands apart.
Our Recent Awards
Over 100,000 networks worldwide choose BackBox
Why BackBox?
Daily, you deal with essential repetitive tasks that can compromise network security, if ignored. BackBox reliably automates these tasks, allowing you to trust the results and focus on more strategic projects.
Vulnerability Remediation
Enhance network cyber resiliency and save time with automated vulnerability remediation and one-click backups, allowing your team to focus on innovation and reduce tedious CVE tracking.
Configuration Compliance
Achieve configuration compliance at scale with no-code automations, pre-built tasks, and auto-remediation, saving time and enhancing cyber resiliency across your network.
Privacy-first Approach
Reinforced protection backed by SOC 2 Type 2 attestation offers independent validation that our security controls and operational processes adhere to high standards of excellence.
Multi-vendor Support
Out-of-the-box support for over 180 vendors and thousands of devices delivers extensive coverage, enabling you to manage your diverse network environment confidently.



For a complete list of supported vendors, download the Vendor Device List.
GARTNER® MARKET GUIDE™
Unlock Your Network’s Full Potential: Download the Gartner® Market Guide
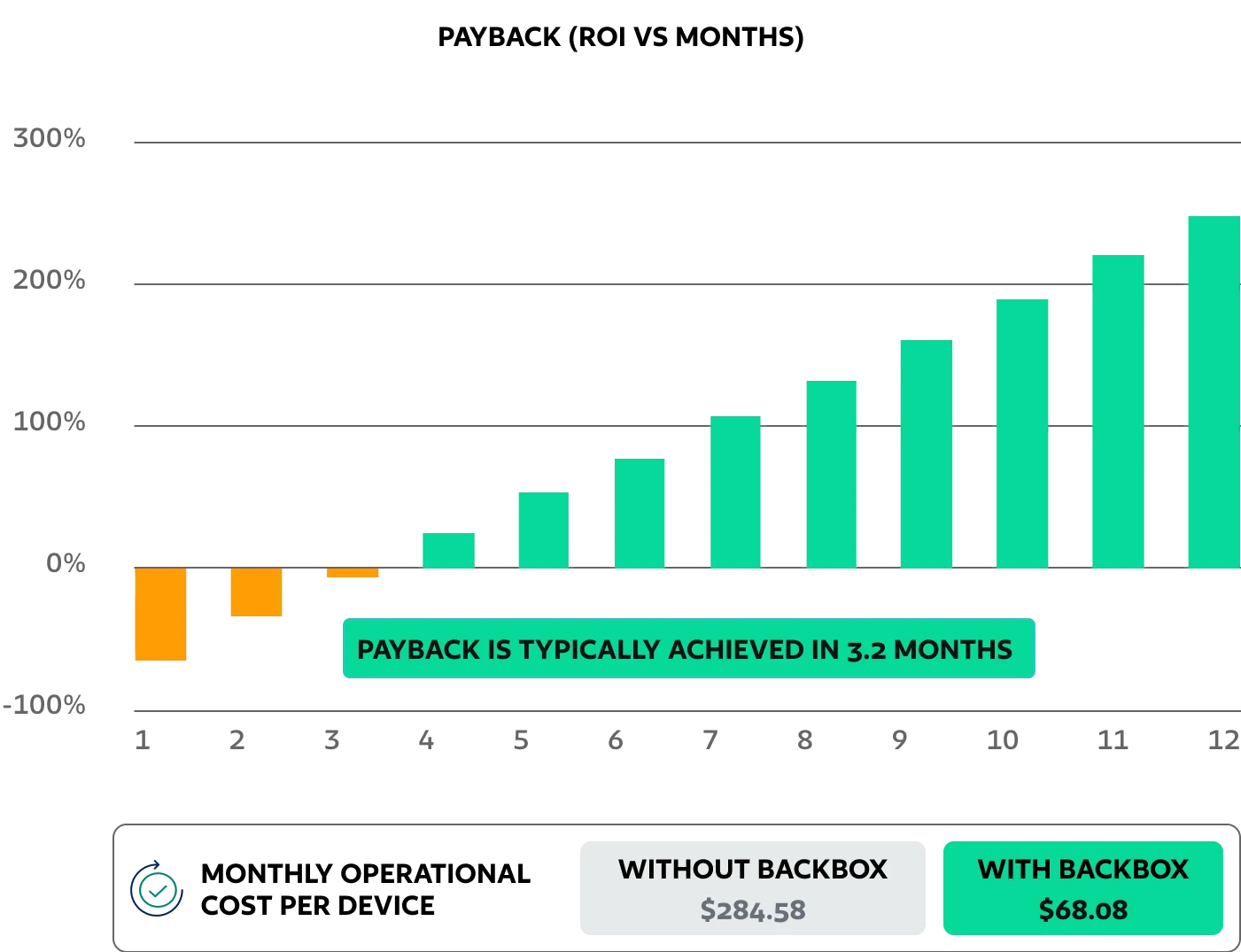
What If You Could Reduce Costs by 76%
Unlocking ROI doesn’t have to be a challenge — BackBox makes it a reality! Automation saves time, boosts efficiency, and delivers strong ROI.
These Organizations Use BackBox to
“With BackBox, bi-weekly patching takes only one hour, compared to at least 35 hours to do manually.”
Discover the difference and join the leaders in network cyber resilience.
Contact us to schedule a demo and discuss what your organization can do with BackBox
















