Security
SecOps’ Path to Cyber Resilience
Network cyber resilience and recovery are critical pieces of a strong security practice. Work with IT to tackle evolving threats, compliance, and privacy.
Trusted By
Over 100,000 networks worldwide choose BackBox
Collaborate for Network Cyber Resilience
Discover how BackBox can automate network maintenance and security work while reducing costs. Ensure ongoing compliance with organizational standards and industry best practices.
Disaster Recovery Preparedness
Implement automated backup policies and recovery processes for all essential network devices to reduce downtime during a cyberattack or hardware failure.
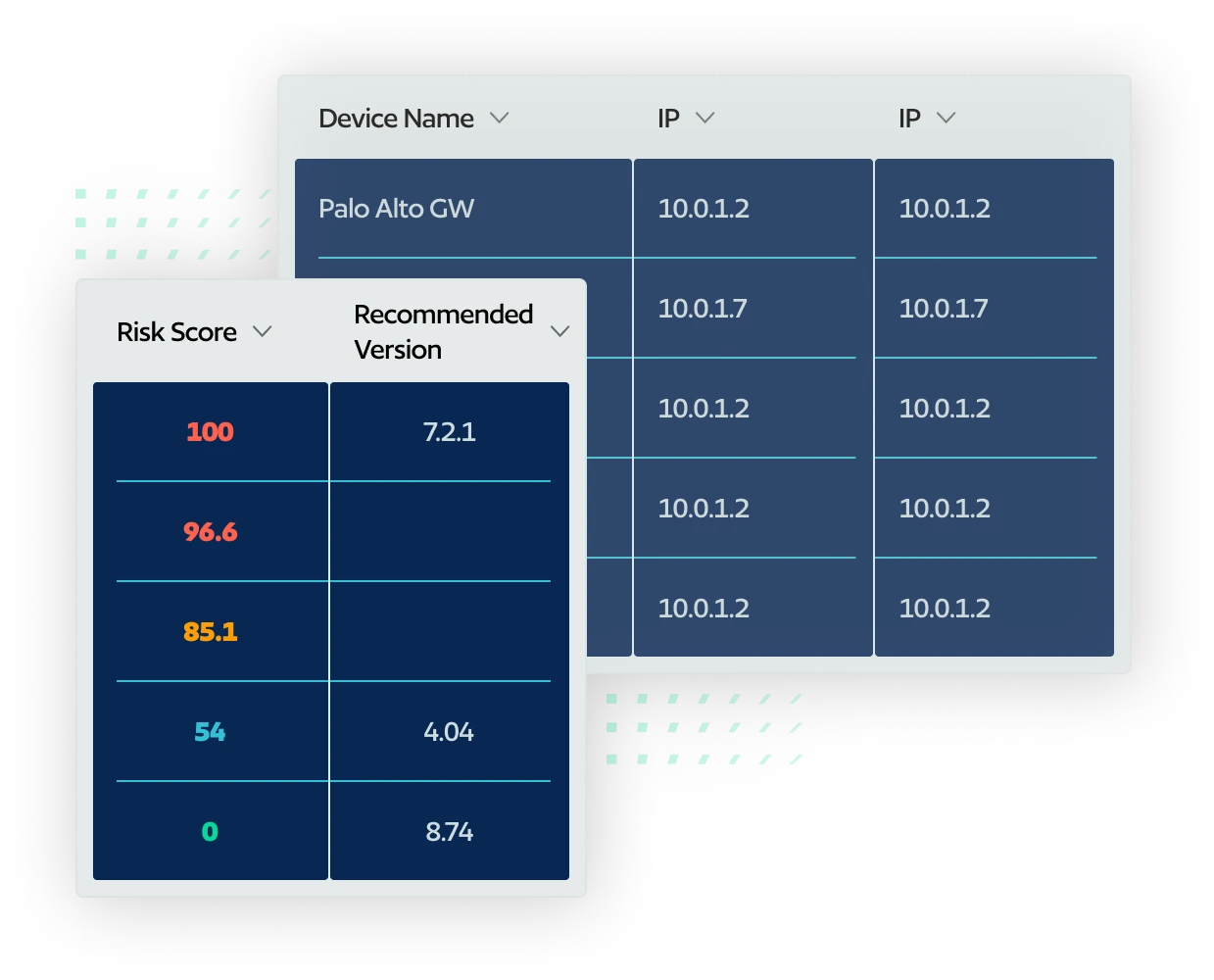
Network Security Posture Monitoring
With centralized dashboards, unlock valuable insights into your organization's compliance and security posture across all network devices.
Incident Response Support
Quickly recover network device configurations after a security breach or misconfiguration to reduce operational disruption and safeguard your organization’s functionality.
Vendor Risk Management
Proactively manage multi-vendor devices throughout the network to ensure uniform security and compliance for a safer environment.

Protect Your Network from Vulnerabilities and Disruptions
BackBox Network Cyber Resilience Platform
Easily automate the security, compliance, and management of your network infrastructure without having to write any code.
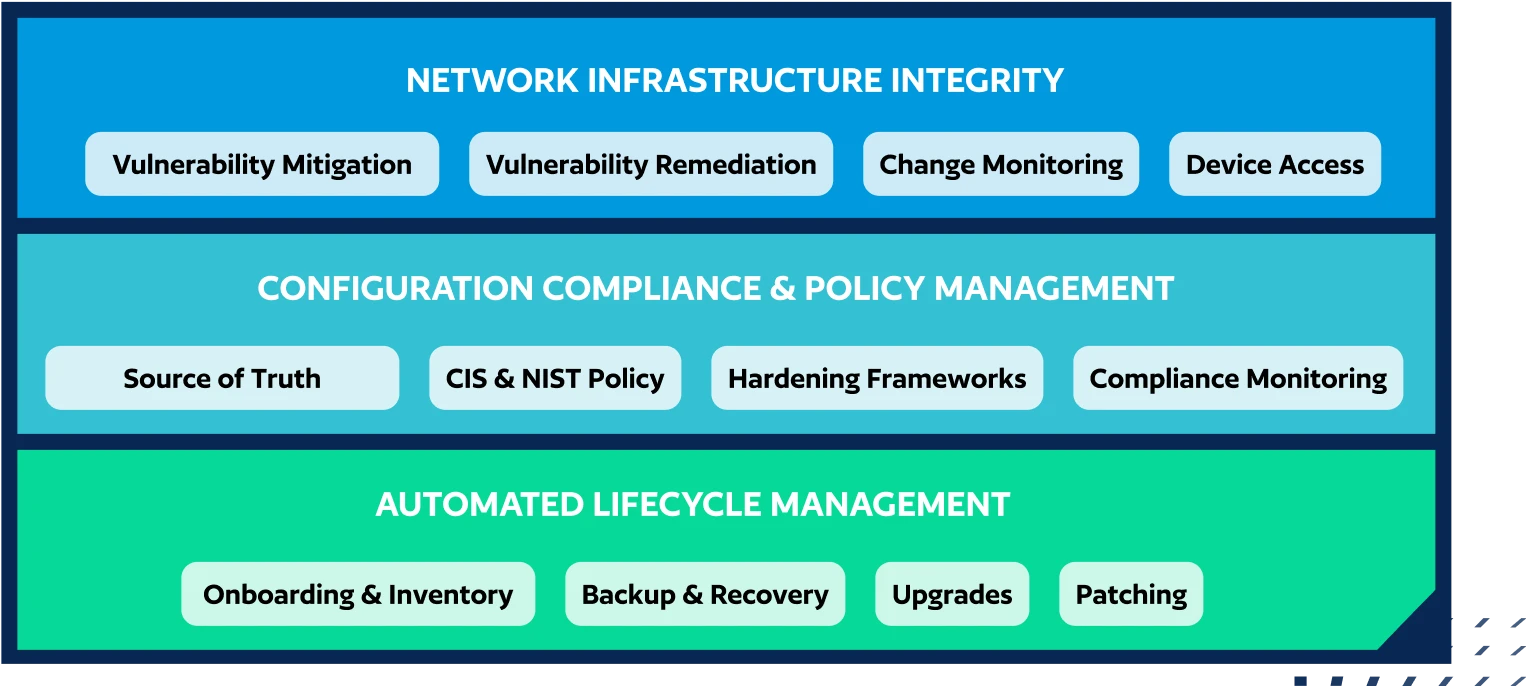
Automated Lifecycle Management
Quickly back up, validate, and restore network devices for easy recovery. Manage, upgrade, and patch major network vendors through a single interface with 3,000+ pre-built automations.
Compliance & Policy Management
Run compliance checks on devices to assess resilience and identify configuration drift, automatically correcting non-compliant configurations to align with industry compliance standards and internal policies.
Network Infrastructure Integrity
Proactively identify active exposures and choose to automate vulnerability mitigation via a configuration change or remediate the vulnerability by updating the device software.
No matter what your needs, BackBox fits your stack
Our Customers Can't Stop Talking About Us
“For those seeking to streamline their network management processes, increase efficiency, and bolster security, BackBox is the go-to solution.”
“BackBox delivers a platform that both security and network teams can use for different reasons – reporting and ensuring devices are upkept and using automation for consistency.”
“BackBox’s user-friendly design simplifies tasks for our teams, enabling easy automation of backups, compliance checks, and device configuration management.”
“Automation is a must for security devices in terms of operation and security. We use BackBox as the main automation gateway. Upgrades, rollbacks, and scripting operations are all conducted through BackBox. And the access solution is straightforward and cost-effective.”
“BackBox efficiently generates configuration backups for your network devices, minimizing manual effort and optimizing capacity.”
Dive Deeper With Expert Guidance
The Network Cyber Resilience Solution CISOs Will Love
See why CISOs trust BackBox to unify security and IT teams with automation, compliance, and risk-based vulnerability management.
Top 5 Ways to Foster and Build Cyber Resilience
To strengthen your organization's cyber resilience, create a collaborative environment between teams.
Buyer’s Guide for Network Cyber Resilience Solutions
Choosing the right automation solution for your network can be challenging. We can help identify key factors to consider.
Take the next step
Cyber resilience is a continuous journey. No matter where you are, we’ll help you take the next step.



