What is Network Vulnerability Management?

Abstract: Network vulnerability management is an important part of network upkeep. Tracking vulnerabilities, understanding their impact on the network, and remediating them helps protect the network from cyberattack. But it is often a time-consuming, labor-intensive process and, therefore, doesn’t get the attention required.
Table of Contents
Network vulnerability management is the discipline of tracking, identifying, understanding, and remediating network device (routers, switches, load balancers) and security device (firewalls, IPSs) vulnerabilities. Networks provide the backbone for today’s digital businesses and present a rich target to malicious actors who wish to take advantage of network and security device vulnerabilities to meet their own goals.
The topic of vulnerability management, however, often conflates endpoints with network devices. These two classes of devices are quite different in how they’re managed and, in particular, in how they’re patched. When a vulnerability is discovered, often the best way to resolve the vulnerability is to update the device software.
Endpoints, where agents are run for just this purpose, are rather straightforward to update. Network devices, including security devices like firewalls, are much more complex to update because you can’t run agent software on the devices. So instead, the devices must be updated manually, an error prone activity, and one-at-a-time. As a result, many companies only have time to update their network devices once or twice a year, making network vulnerability remediation a challenge.
According to Kenna Security’s ‘Prioritization to Prediction, winning the remediation race’ security report, 25% of all vulnerabilities remain open for longer than one year. That’s across endpoints and network devices. However, in the case of Cisco, Kenna reports that 50% of vulnerabilities remain unpatched longer than one year. The lesson Kenna calls out is that it’s important to make it easy to patch.
“Unpatched software is a top three access route for hackers and patching”, says the UK’s National Cyber Security Centre (NCSC) “[updating and applying security patches] remains the single most important thing you can do to secure your technology.” (The Stack, Jan 9, 2023)
Network and security devices as a whole are hard to patch, BackBox simplifies this important process to improve network security.
A New Network Vulnerability Management Approach: Risk management vs threat exposure management
Gartner believes people should “abandon traditional risk management practices as part of cybersecurity management” and instead talk about threat exposure to guide security activities.
The reason being risk and risk mitigation is about future probabilities and investing to minimize the probability of a breach. Predicting the future is a fool’s game, with uncertain and unknowable outcomes. Risk modeling easily becomes security theater rather than a tool for discovering the truth.
In contrast, exposure management is about understanding and mitigating a company’s defined vulnerabilities. Network vulnerability management doesn’t deal in likelihoods, it deals in absolutes. Defined vulnerabilities are certainties, not risk, that can be surgically and proactively addressed. Network vulnerability management points out the vulnerabilities that are relevant to specific network devices and enables those vulnerabilities to be patched or remediated.
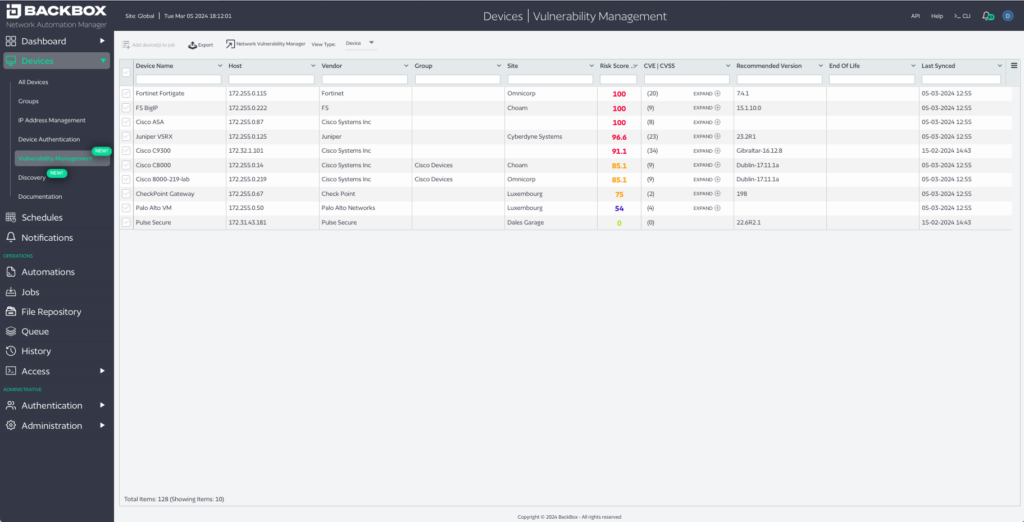
BackBox Network Vulnerability Manager (NVM) gives companies a list of their potential exposures based on their actual inventory (and by inventory we mean: vendor, device, and OS version) and the remediation tools to mitigate these known exposures. We are grounded in the reality of threats that exist today by focusing on known vulnerabilities and the meta-data describing their risk rather than trying to predict the potential for risk in the future.
Read: 5 Questions to Help Keep Your Network Safe
With BackBox NVM, we have a few key principles that guide our product evolution.
Focus on simplicity
Risk management systems are commonly over-engineered. While there are places for comprehensive security solutions, the network team also needs an easy-to-use tool that helps them prioritize their work in order to maximize their impact on vulnerabilities.
BackBox NVM incorporates user-friendly dashboards, pre-built automations, and script-free ways to build new automations. In so doing, we eliminate obsolete manual processes and provide visibility into exposure to threats. Network teams have a straightforward tool to help them address network vulnerabilities within their purview.
Focus on real-world threat impact
Reducing the impact of vulnerabilities on the network is critical because the high-speed automation of attacks means the probability of a threat impacting an enterprise is effectively 100%. An easy-to-use tool must also help the network team get ahead of potential attacks by patching vulnerabilities quickly.
BackBox NVM taps into a rich data feed to understand whether a CVE is known to have been exploited in the wild, what the impact of the exploit is, and how easy it is to exploit. We factor that into the risk score for the customer, so that network engineers can prioritize vulnerabilities for remediation.
Focus on measuring improvements
It’s not enough for the tool to be simple and reduce the impact of the attack, it must also transparently report on the enterprise’s evolving threat exposure. This is achieved by mapping the impact an exploit would have had in an enterprise with the vulnerabilities that have been remediated to show a reduction in threat exposure. When starting with BackBox NVM, a customer gets a list of exposures at the network and device level. Each device and network is given a risk score and as CVEs are marked as mitigated it becomes straightforward to measure mitigation results. Whether measuring by the number of critical vulnerabilities on the network, the device scores, or some other metric, the customer gets transparency into improvements in their security posture.
2 Recommendations to Set Your Network Vulnerability Management Program on the Right Course
With the shift from risk management to threat exposure management in mind, there are two steps every network team should take to improve their network security posture:
- Mitigate defined cybersecurity threats via programs that reduce an enterprise’s exposure to associated exploit and threat vectors.
- Use threat intelligence and research to quickly identify threats that emerge from the cloud of uncertainty. It’s important to monitor inventory and security alerts daily, bringing them together to surface actionable threat/vulnerability information. Don’t deal in probabilities of an exploit, look for specific facts about exploits as they relate to your specific network configuration.
The goal is to take what you know to make your network more secure, rather than trying to predict the future (when we know the future is uncertain). With a network vulnerability management tool, network teams can easily find out what vulnerabilities apply to their networks, how relevant these vulnerabilities are, and what steps should be taken to mitigate or remediate the vulnerabilities. Keeping this at the forefront of your network vulnerability management program will ensure it stays on the right track.
What are network vulnerabilities?
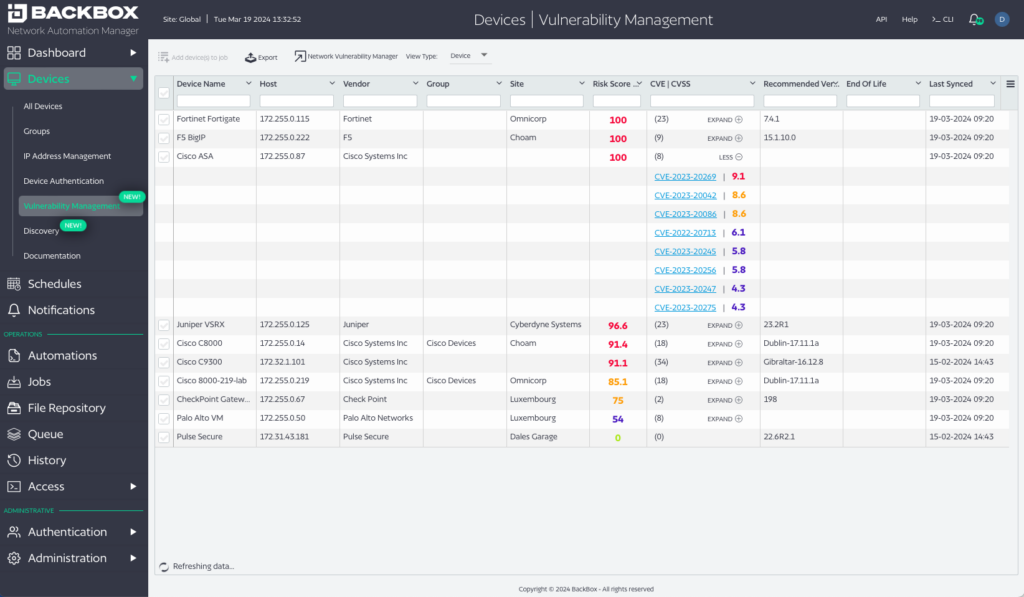
A network vulnerability is a bug in the device’s code base reported by device vendors that can be exploited by bad actors. Vulnerabilities are reported by vendor and a CVE Record is published. CVE Records, or simply ‘CVEs’, are used to communicate consistent descriptions of vulnerabilities. Information technology and cybersecurity professionals use CVEs to ensure they are discussing the same issue, and to coordinate their efforts to prioritize and address the vulnerabilities.
One of the challenges with network vulnerability management is that while the CVE is the source of truth for the vulnerability, it’s not the only place to get information about the vulnerability. CISA, for example, provides other information such as whether a CVE is known to be actively exploited. Vendors provide still more information. Many vulnerability management solutions focus solely on the CVE and therefore don’t provide enough context to help network engineers make the best remediation decisions for their environment.
Mitigation or remediation? What’s the difference?
The language around remediation is a little nuanced, so it’s worth taking a minute to clarify usage of the words ‘mitigation’ and ‘remediation’.
Mitigation is when you take steps to reconfigure a device to protect it from a known vulnerability. Recently there was a vulnerability in the http server on Cisco devices. Mitigating this vulnerability would mean turning off http server. Simple, but what if you need the vulnerable feature? By definition, mitigation is a temporary fix.
Remediation, on the other hand, is a permanent fix of the vulnerability and is usually only accomplished by an update to the device operating system. Remediating a vulnerability means eliminating the vulnerability from the network by getting rid of the software version that contains the vulnerability.
Remediation is hard, because updating device software is often a complex, time-consuming process requiring after-hours work and large change windows that are difficult to arrange.
Why automation is an important enabler of Network Vulnerability Management
Many companies have not implemented or invested deeply in network automation , opening them up to security breaches, ransomware, and other serious issues.
Network automation is the foundation for mitigation and remediation at scale, as well as inventory collection which kicks off the whole vulnerability mapping process. Automation also brings a host of benefits by reducing manual errors and increasing team productivity.
What happens, as in the Cisco case above, if you need to visit all your public facing Cisco routers to turn off http and https servers? At scale that quickly becomes a time consuming, error-prone activity. Here’s an example of how much time can be saved with automation using a similar situation.
For service providers, automation is an opportunity to shine with high-touch services that delight customers.
The ROI for network automation is easily measurable. Edafio, a leading managed service provider to mid-sized and enterprise clients, had a significant ROI by implementing automation for their patching and device updates. And, that ROI doesn’t even measure the value of limiting the team’s after-hours work or enabling the team to have more time to focus on higher value strategic work over mundane software updates.
Read: 7 steps to improving network security through automation
What are the steps of the vulnerability management process?
Track vulnerabilities
The vulnerability management process starts with collecting the network inventory and mapping it against the vulnerability feed.
There are a few things in there worth teasing out.
Network inventory is collected automatically by a solution like BackBox, so we know exactly what vendors, devices, and versions are present on the network.
A vulnerability feed is a stream of information about vulnerabilities. Many times this feed is simply a list of CVEs, and as mentioned above, that’s not enough. BackBox also incorporates CVEs from the National Vulnerability Database and enriches that information with context from elsewhere, like CISA, vendor information feeds, and more.
An enriched feed is effectively tracking vulnerabilities and their status – are they being exploited? What’s the potential for harm? How easy are they to exploit?
Mapping the actual inventory against the vulnerability feed is the first step in the network vulnerability management process.
Score the devices
Using this feed and the inventory in your network, the devices and networks are scored to get a measure of their vulnerability status. With this score, which considers the number of CVEs, their criticality, and other metadata, network engineers can mark certain CVEs as irrelevant or to be revisited later and prioritize remediation and mitigation efforts on those with the greatest potential impact to the organization.
Mitigate or remediate
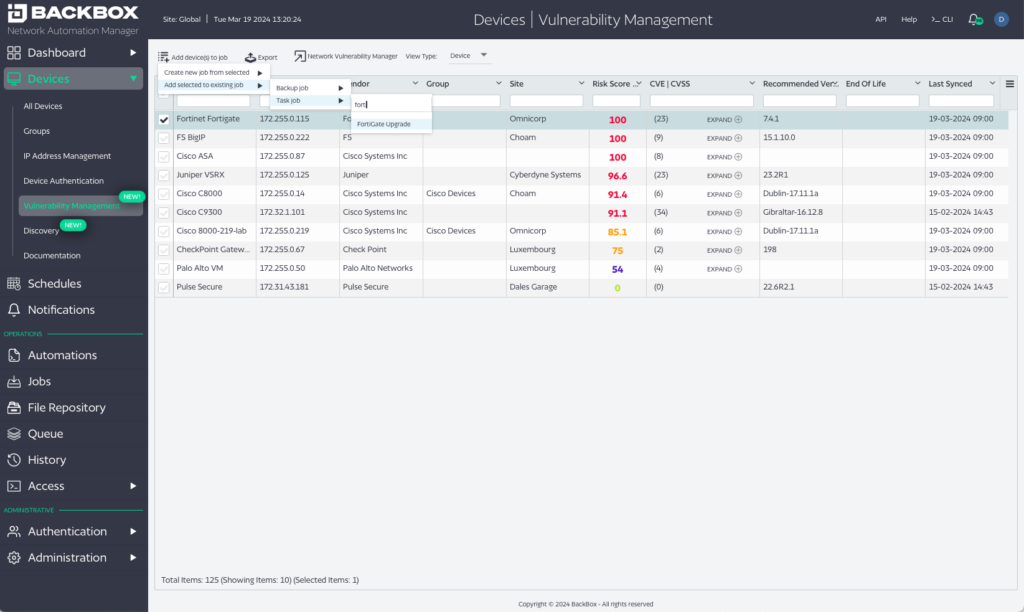
Sometimes vendors include mitigation instructions in their CVEs, but most times mitigation is left to remediation via a software update. In either case, BackBox provides automations to simplify the process.
Network Vulnerability Management as a Tool to Defeat Ransomware
Ransomware is not often considered the domain of network teams. However, software updates ensure that firewalls and security devices that do deep content inspection contain the latest virus and content definitions helping to prevent malware from entering the organization.
Software updates are downstream from vulnerability tracking, and are often associated with the remediation portion of the lifecycle of vulnerability management. It’s important to realize that a network automation platform like BackBox simplifies software updates, which ensures that the network team is a good citizen when it comes to doing what it can to prevent ransomware from entering the organization.
To learn more about BackBox and Ransomware:
- Watch the webinar: “Manage Network Vulnerabilities to Help Protect You from Ransomware”
- Read the blog post: “Ransomware and Your Network”
- Read this deep dive by our CTO on how-to use BackBox to protect your network from ransomware.
What are vulnerability management benefits?
Vulnerability management aids enterprises in pinpointing and addressing potential security vulnerabilities proactively, preventing them from evolving into significant cybersecurity threats. This proactive approach not only safeguards against security breaches but also protects a company’s reputation and financial standing.
Effective vulnerability management enhances adherence to compliance protocols and regulations. Furthermore, it provides organizations with a clearer comprehension of their overall security risk landscape and areas where improvements can have an impact on the organization’s overall security posture.
In today’s interconnected landscape, relying solely on sporadic security scans and reacting to cyber threats is inadequate as a cybersecurity strategy. Vulnerability management offers three key benefits:
- Improved security. Often vulnerability tracking is done in a spreadsheet, without a good understanding of the exact network inventory you’re protecting. An automated network vulnerability solution helps map your exact inventory against known vulnerabilities to help visualize your security posture and gamify improvements. BackBox NVM also automatically analyzes new devices as they’re onboarded to ensure that no new known vulnerabilities are added to the network as they’re connected.
- Reporting and collaboration. Security is a team sport, yet security teams are increasingly overwhelmed by the growing attack surface they need address to protect their organization from rising attacks. Network teams can help. With a network vulnerability management tool that allows them to report on vulnerabilities and necessary remediation activities for devices within their scope of responsibility, network teams can keep their peers in security and compliance up-to-date proactively and help alleviate the burden they face.
- Operational efficiency. Device updates are complex, time-consuming activities. Prioritizing and simplifying them based on the impact they have to security is critical in improving the network team’s effectiveness against threats and strengthening the organization’s overall security posture.
What should I look for in a network vulnerability management tool?
Network vulnerability management is challenging for a few reasons. Devices are difficult to update, organizations often have a very heterogeneous environment with multiple vendors for network and security gear, and most security products are not purpose-built for network teams which means people need to connect security products to what it means in their environment.
That said, a good network vulnerability management tool will do these three things:
- Track more than CVEs. Understanding CVEs is important, but they don’t provide the context that network engineers need to make decisions. Are two critical CVEs equal? Maybe one is easier to exploit, or worse, is already being exploited. This is information engineers need to in order to come up with a plan that best protects the enterprise. And, recently, there’s been some concern around simple CVE enrichment, let alone the more complex enrichment that BackBox does. A good network vulnerability management solution will start with CVEs and incorporate other contextual information from elsewhere to enrich the vulnerability tracking feed.
- Score vulnerabilities to help prioritize remediation activities. Not all devices are created equally. For example, public internet facing devices with vulnerabilities pose a greater risk to the organization than that same device behind a DMZ. Considering CVEs, CVE context (or metadata), and network topology to provide a risk score is critical to help network engineers understand the specific impact of a CVE or, more likely, a set of CVEs, on their network and devices so that they can best prioritize remediation activities.
- Close the loop between identification and remediation. Too many solutions only provide a list of vulnerabilities and leave the ‘taking action’ part of fixing vulnerabilities to manual steps completed by network engineers. Manual remediation is obsolete, slow, and error prone. A good network vulnerability management solution will ‘close-the-loop’ between vulnerability tracking, scoring, and remediation and automate remediation so that identified vulnerabilities are fixed with as little effort as possible. Similarly, if mitigation is necessary, a good solution will provide the search and automations necessary to determine where a CVE is relevant, and automate the actions taken to mitigate the vulnerability.
FAQ
1. What’s the difference between BackBox NVM and something like Qualys or Tenable?
Tenable and Qualys both require agents, and don’t close the loop with remediation. We are agent-less, meaning that we can work specifically with network and security devices where you can’t install agents, and help you with the remediation using built-in, fully customizable, OS Update automations.
Even if you’re already using these products in your SOC, NVM has been purpose built for network teams and works with a dynamic inventory assessment so that you can be sure that you’re paying attention to the vulnerabilities that matter to your exact inventory (vendor, device, OS version).
NVM is, like BackBox Network Automation Manager, built on a multi-tenant infrastructure and as such also serves the needs of service providers.
Finally, BackBox NVM is simple to install and get running.
2. How is the risk score calculated?
The risk score is calculated using the following information and more:
- How many CVEs are on a device?
- What are the CVSS scores relevant for that device?
- Are the CVEs critical, high, medium, or low risks based on CVSS score?
- Is the device internet facing?
- Is CISA reporting that the vulnerability is known to be exploited in the wild?
- How easy is it to exploit?
- What’s the impact of being exploited?
- What other vendor information is available about the vulnerability?
- Is the device end-of-life?
- Is an update or workaround available for the vulnerability?
3. What’s involved in getting started with BackBox NVM? What licenses are required?
BackBox Premium licensing is required. For those on legacy pricing, IntelliCheck licensing is a pre-requisite. NVM has an additional per-device charge on top of either Premium or IntelliCheck licensing.
Getting started is simple. There’s a prebuilt job in the BackBox Network Automation Platform that would be run that collects inventory and sends it to NVM for mapping against the vulnerability feed. This job should be run regularly, so that your NVM inventory is up-to-date with changes in the network. There is no performance hit for running this job, because inventory is collected with backups, and so adds no overhead.
The first time the job is run, device inventory along with risk scoring and vulnerability information is populated in the NVM product page. This initial population can take up to a day as the inventory is compiled and completed. Subsequent inventory updates are near-instantaneous.
4. How often is the vulnerability database updated?
The vulnerability database is updated as often as vulnerabilities are added to the national vulnerability database (NVD) or announced by vendors.