Solutions
Zero Trust NetOps (ZTNO™)
Six Actionable Pillars to Automate Zero Trust in a NetOps Environment
Do you know who’s logging in and changing your network device configurations?
Are you certain that your devices remain compliant with the configurations you want?
BackBox ZTNO supports and extends zero trust by enabling key controls around owned and controlled network devices and the network engineers that manage them. Risk and trust are constantly assessed through onboarding and daily operations. ZTNO is implemented with a combination of automation, vulnerability management, and privileged access management.
Simple admin compliance
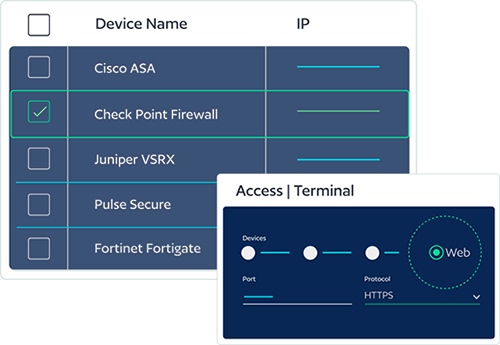
Using BackBox Access Manager as a jumpbox for configuring devices ensures that every session is logged and recorded.
Onboard devices with the right configuration
Automating the governance of the onboarding process ensures that devices are configured correctly while saving administrators time with automation.
Keep devices compliant
Automated remediation gives administrators the option of remediating configuration drift when it’s discovered.
Solution overview
The six pillars of Zero Trust NetOps™ is designed to keep your network compliant both for the devices on the network and the administrators who keep it all running.
Access Management
Secure access needs to be provided whether accessing network devices via API, WebURL, or CLI. BackBox accomplishes this by integrating role-based access controls with credential vaults and providing a secure, credentialed API. Additionally, automations can have permissions associated with them, so that administrators can perform their jobs and have exactly the right permissions (through association with the automation).
Audit and Control
Humans accessing network devices should do so only in an auditable manner. This is done with controls to log all changes to an immutable log, and even to record administrator sessions for replay. Roll-back of changes is also made possible through this centralized access point.
Device configurations should be made consistent with a ‘golden configuration’ during the onboarding process. This is done via policy enforcement that ensures the appropriate configurations. Done in an automated manner, this eliminates manual errors and improves the speed of onboarding new devices to the network.
Vulnerability Management Onboarding
During the onboarding process, devices are checked for known vulnerabilities which are then remediated prior to being added to the network. Vulnerabilities that aren’t relevant can be ignored, while those that are relevant can be patched or updated based on vendor recommendations for mitigation.


Continuous Assessment
Once onboarded, devices are continuously assessed for both configuration compliance and new vulnerabilities. When configuration drift is discovered, configurations can be groomed into compliance automatically or notifications can be sent to alert administrators of non- compliance. Similarly with vulnerabilities, as new vulnerabilities are discovered, when deemed relevant they can be patched.
Reporting and Visibility
Rich reporting and visibility ensures that teams communicate and are aware of the steps taken to protect the network. Reports can be configured such that actionable data is highlighted for security and networking teams to keep the network as secure as possible.
“Zero trust replaces implicit trust with continuously assessed risk and trust levels, based on identity and context. I&O leaders must work closely with security leaders to incorporate zero trust principles into their networks.”
Key Features
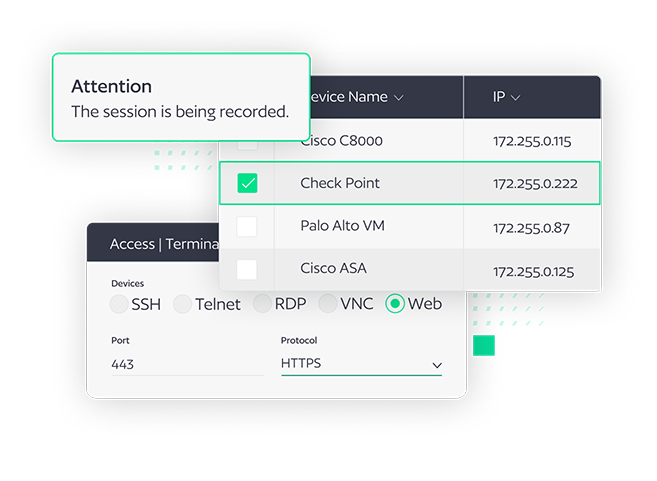
Access Manager
BackBox Access Manager acts as a jumpbox for access to devices, ensuring that every session is logged and recorded for both compliance and training. Access Manager enables role-based access control to devices, and allows for a library of commands to simplify device administration.
Compliance Automation
With an Automation Library of over 3,000 automations, BackBox delivers many compliance automations including DISA STIGs, CIS Benchmarks, PCI DSS, and more. Compliance automations have optional remediation attached so that configuration drift can be eliminated automatically.
Network Vulnerability Manager (NVM)
As part of compliance, BackBox NVM ensures that no known vulnerabilities are introduced into the network as new devices are added to the network.
Why BackBox?
Whether or not you have a fully articulated network automation strategy, every day you face an onslaught of repetitive but critical tasks that, if neglected, put the network at risk. BackBox is here to reliably automate that operational work so you have confidence in the outcomes and can focus on more forward-looking projects.
Rock-solid Backups
Five validation checks on each backup with a single-click restore makes us the most trusted network backup solution in the industry.
Firewall Automation
From reliable backups to streamlined OS updates and onto automated compliance, BackBox can simplify the administration of your firewalls.
Explore other solutions
NCM
Network Configuration Management
NVM


