Empower Your Team With Network Automation
There are a variety of situations where network automation enhances the ability of the business to be more agile, from integrated Vulnerability Management – bringing together vulnerability and threat information with active device remediation – to NetOps.
Explore the Buyer's Guide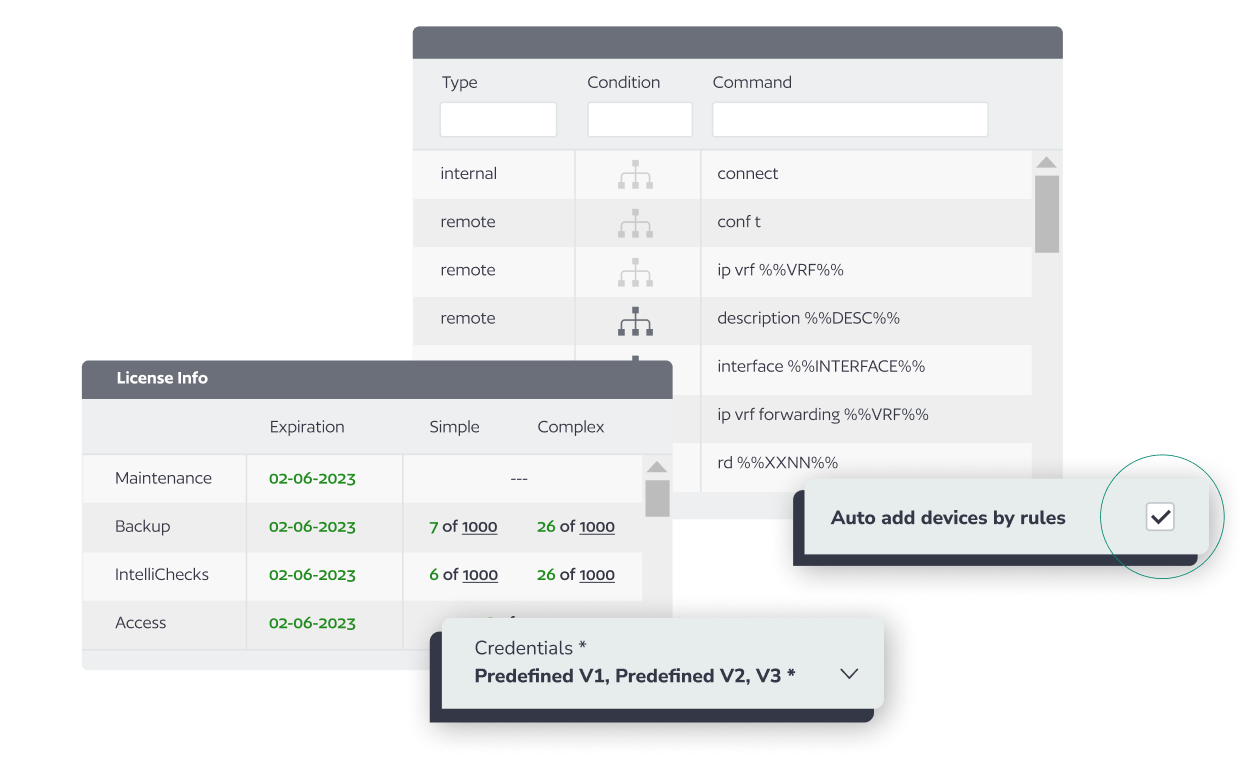
Network Automation
BackBox is a purpose-built automation platform designed to power even the largest network, while still being easy to deploy and get value straight "out of the box."
There are three key components to the BackBox Network Automation Platform:
Automation Engine
The automation engine is a distributed platform for executing automations across the network in a way that’s both performant and privacy-preserving.
Automation Library
A library of pre-built automations that attack the most common administrative use cases, as well as help administrators with common tasks that are helpful in their daily activities.
Automation Builder
There’s no scripting required to automate tasks with BackBox. Simply type the API or CLI commands you wish to automate, and we’ll create the automations for you. Need help? Our support team works with customers to help create automations.
Prebuilt automations solve for the most common use cases, including:
- Device backups, with single-click restore
- Compliance, audit, and remediation
- Task automation
- OS and Firmware updates and patching
- Vulnerability management
Automated Firewall Management
In addition to network devices, BackBox automates the administration of security devices, including firewalls. Specifically, the BackBox Automation Library has prebuilt automations for the most common use cases for Check Point, Palo Alto, Juniper, Cisco, Fortinet and other firewall vendors:
- Backups, with 1-click restore
- OS and firmware updates and patching
- Vulnerability management
- Configuration compliance & remediation
- Firewall rules management
BackBox automations intelligently perform each of these use cases to improve performance and deliver the right outcomes. For example, backing up a firewall is done in a way that ensures a single-click restore in the event of a failure, and that firewall replacements can be reconfigured from bare metal using a backup. Similarly, OS update automations separate the most common obstacles of error-free updates to help administrators simplify the update process. BackBox automations are also high-availability aware and can update HA-pairs in a way that’s seamless to network operations.
Network Configuration Management
Improve network operations with network configuration management. With BackBox network administrators can:
- Use network automation to backup and restore device configurations,
- Automate device configuration and change management, and
- Ensure device configuration compliance by maintaining a device baseline and grooming configurations back to the baseline as they drift.
Network administrators can easily browse configurations and answer the most important question when troubleshooting the network – “What changed?”. No longer reliant on inventory spreadsheets and their accuracy, BackBox provides an accurate, up-to-date, and reliable inventory and configuration tracking capability.
BackBox also integrates with the most common network monitoring tools, like Paessler PRTG and LogicMonitor, to deliver a best-in-class network management experience.
Network Vulnerability Manager
With BackBox Network Vulnerability Manager you can prioritize device patching based on actual risk.
- Identify new vulnerabilities and classify by threat level as they surface.
- Map those against your unique and dynamic network inventory.
- Plan and automate hardware replacements around vendor driven EOL (End of Life) data.
- Automate mitigation through configuration changes and network and firewall OS upgrades and patches.
Closed-Loop Vulnerability Management
Starting with device discovery, BackBox models the configuration inventory of your network. The inventory is mapped against a threat and vulnerability intelligence feed that uses CVEs and other security information to determine the threat level against your specific inventory. Risk level, recommended updates and patches, and product end-of-life information is then used to provided recommended automations that remediate the discovered vulnerabilities.
Network Vulnerability Manager is purpose-built for network teams to easily discover vulnerabilities in their network, prioritize CVEs according to their unique risk profile, and automate multiple levels of remediation, no matter the network complexity. Check out our FAQ page to learn more.
Network Source of Truth
A network source of truth is critical to securing and operating a network at scale.
BackBox acts as a network source of truth by dynamically discovering and modeling devices as often as you wish. Dynamically discovering and then modeling devices ensures that administrators KNOW exactly what devices make up their network. BackBox even collects end-of-life product information to help manage the overall device lifecycle.
By modeling devices, it becomes about more than the specific inventory, but also about the configuration of the devices. Using the BackBox API, we can inform any CMDB or other centralized configuration database of the network inventory.
Network Compliance Management
The larger the network, the more difficult it is to ensure compliance. For organizations with multiple large networks to manage, such as MSPs and MSSPs, the resulting complexity requires a powerful solution.
BackBox’s extensive Automation Library can automatically check your networks’ devices against critical parameters, generate and send (and archive) reports detailing their level of compliance, and automatically remediate discrepancies (or open a trouble ticket in ServiceNow or other ITSM to await administrator confirmation).
In this way, BackBox allows you to easily achieve and maintain compliance with both external regulations (such as HIPAA, DISA STIGs, and CIS), as well as internally defined policy (such as password complexity), across networks of all sizes.
NetOps Automation
With an API-first approach to network automation, BackBox is the perfect complement to a NetOps environment. Any automation can be accessed via API so that NetOps tools can actively change and remediate the network. Similarly, automations can trigger calls out to NetOps tools to share information and trigger NetOps processes in the NOC.
Managed Service Providers
Built from the ground up as a multitenant solution, BackBox enables simplified management of multiple, complex networks at scale, making it especially valuable to managed service providers (MSPs) and managed security service providers (MSSPs).
Solutions offered to service providers, and using BackBox, by service providers to their customers, include:
- Device backup and disaster recovery
- OS and firmware updates and patching
- Vulnerability management
- Compliance, audit, and remediation
BackBox integrates with the MSP tech stack through our open API to ensure seamless operations within the MSP NOC.