5 Questions to Help Keep Your Network Safe
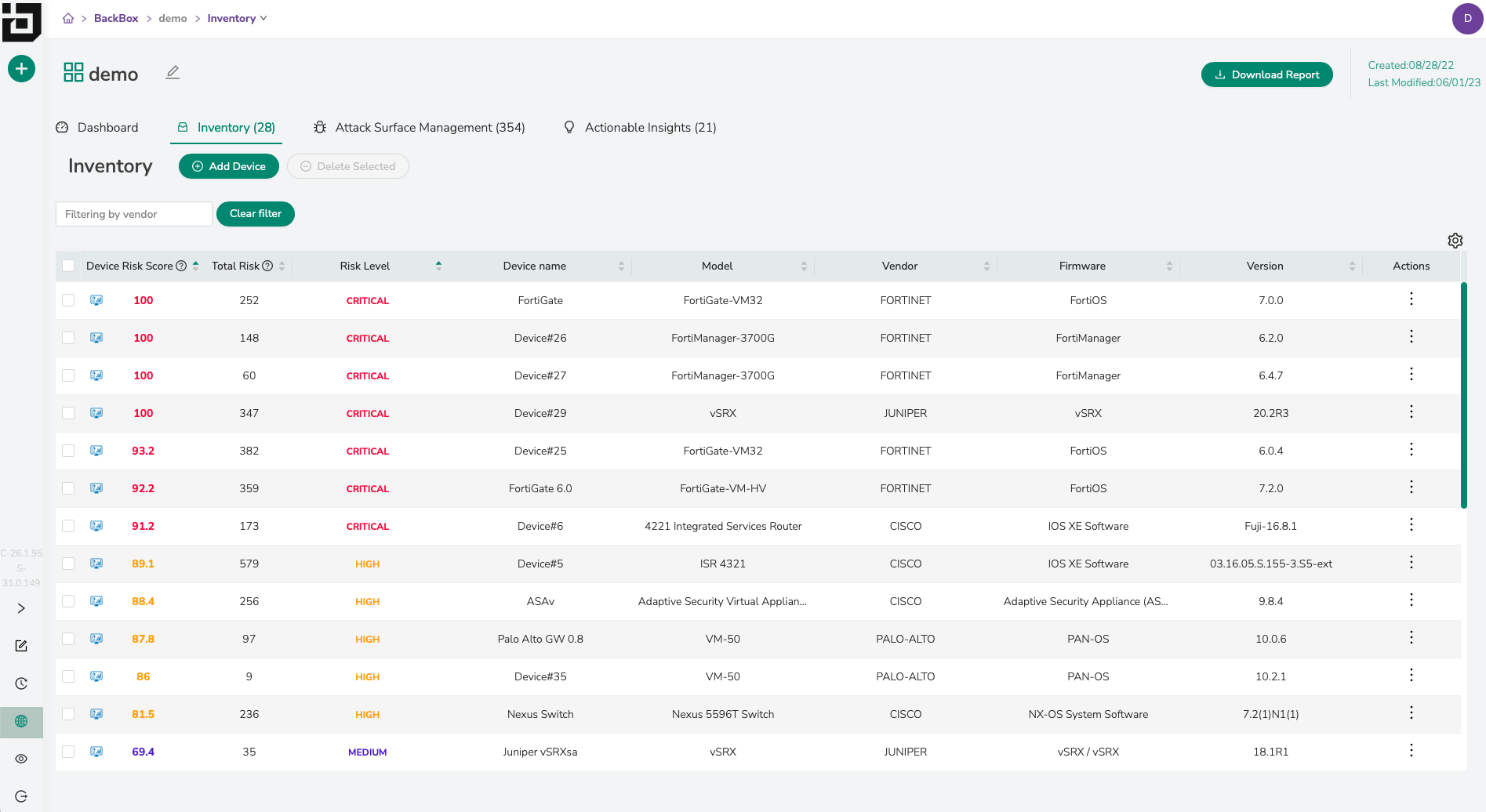
Network Vulnerability Manager (NVM) is built specifically for network administrators and designed to help them prioritize OS updates based on actual, measured, risk to the organization.
Updating devices sounds easy. Just update the software, right? Every vendor tool has that capability. It should be easy.
Partially because the quality of update tooling varies by vendor, and partially because updating at scale is time intensive and can be disruptive. We all used to take the the position that if the network’s working, don’t touch it.
However, in today’s security environment with over 2,500 CVEs released per month and easy access to bots and exploit tooling we have to assume that any known vulnerability is going to be exploited (Gartner). Therefore the risk of not patching known vulnerabilities outweighs that of the potential of breaking things with an update.
It’s unfortunate that patching device OS’s is so hard because:
“Unpatched software is a top three access route for hackers and patching”, says the UK’s National Cyber Security Centre (NCSC) “updating and applying security patches remains the single most important thing you can do to secure your technology.” (Source)
We designed Network Vulnerability Manager to help administrators answer the following five questions, as a way to making OS updates easier by highlighting the security value doing them brings to the business:
- Am I vulnerable? Where?
Using dynamic inventory presented by the BackBox Automation Manager we map CVEs and other threat intelligence against devices to highlight each device’s security profile. - How do I prioritize vulnerabilities?
Each device is given a risk score, and the level of risk and CVSS score is surfaced from our security database so that organizations can quickly measure their level of vulnerability. Organizations now have a punch-list against actual inventory so they can decide to make sure all devices have a CVSS score lower than 7 (a standard security practice) or can eliminate all critical vulnerabilities, or whatever measured approach they’d like. - How do I communicate with other stakeholders to ensure vulnerabilities are patched in a timely manner?
Rather than wave your hands with a invocation of “we need to be on a newer version of software to minimize vulnerabilities”, NVM provides scoring that can be used to demonstrate the risk exposure to the business. Gain stakeholder buy-in with measurements and facts, rather than fear. - How do I deploy the patch quickly, efficiently, and without mistakes?
BackBox Automation Manager has pre-built automations to cover many complex update scenarios for all the common vendors (and many uncommon ones!), including multi-step upgrades, upgrading high-availability pairs, and incorporating backups and pre- and post-checks, along with automatic fall-back in the event of a bad update, notifications, and reporting. - How do I track vulnerabilities over time?
NVM is a closed-loop solution. Network Automation Manager feeds inventory (including device OS version) into Network Vulnerability Manager at an interval of your choosing so that as you update devices, they’re reflected in your vulnerability analysis. With over 2,500 CVEs released monthly (NIST), and that number growing 20% a year, it’s important to constantly be tracking inventory against a vulnerability and threat intelligence database so that you can best protect the enterprise.


