5 Questions to Help Keep Your Network Safe
Network vulnerability management is intended to help network administrators prioritize OS updates based on actual risk to the organization.
In theory, updating devices sounds easy. Every vendor provides software updates so you can implement them. In practice, however, it’s not.
Because the quality of update tooling varies by vendor and updating at scale can be time-intensive and potentially disruptive to the business, the prevailing thinking has been that if the network’s working, don’t touch it.
However, in today’s security environment, with over 3,300 CVEs released per month and AI-enabled attacks dramatically shortening time-to-exploit, we have to assume that known network device vulnerabilities are being exploited more quickly. Therefore, the risk of not patching known vulnerabilities outweighs the potential risk of breaking things with an update.
Organizations are now in a situation where 56% report that their most recent data breach was caused by exploiting a known vulnerability that was not properly patched or addressed. We need better tools to simplify addressing network device vulnerabilities because the pain is real. BackBox vulnerability intelligence answers the following five questions that are holding back patching regimes so that network administrators build confidence to tackle device updates proactively:
- Am I vulnerable? Where?
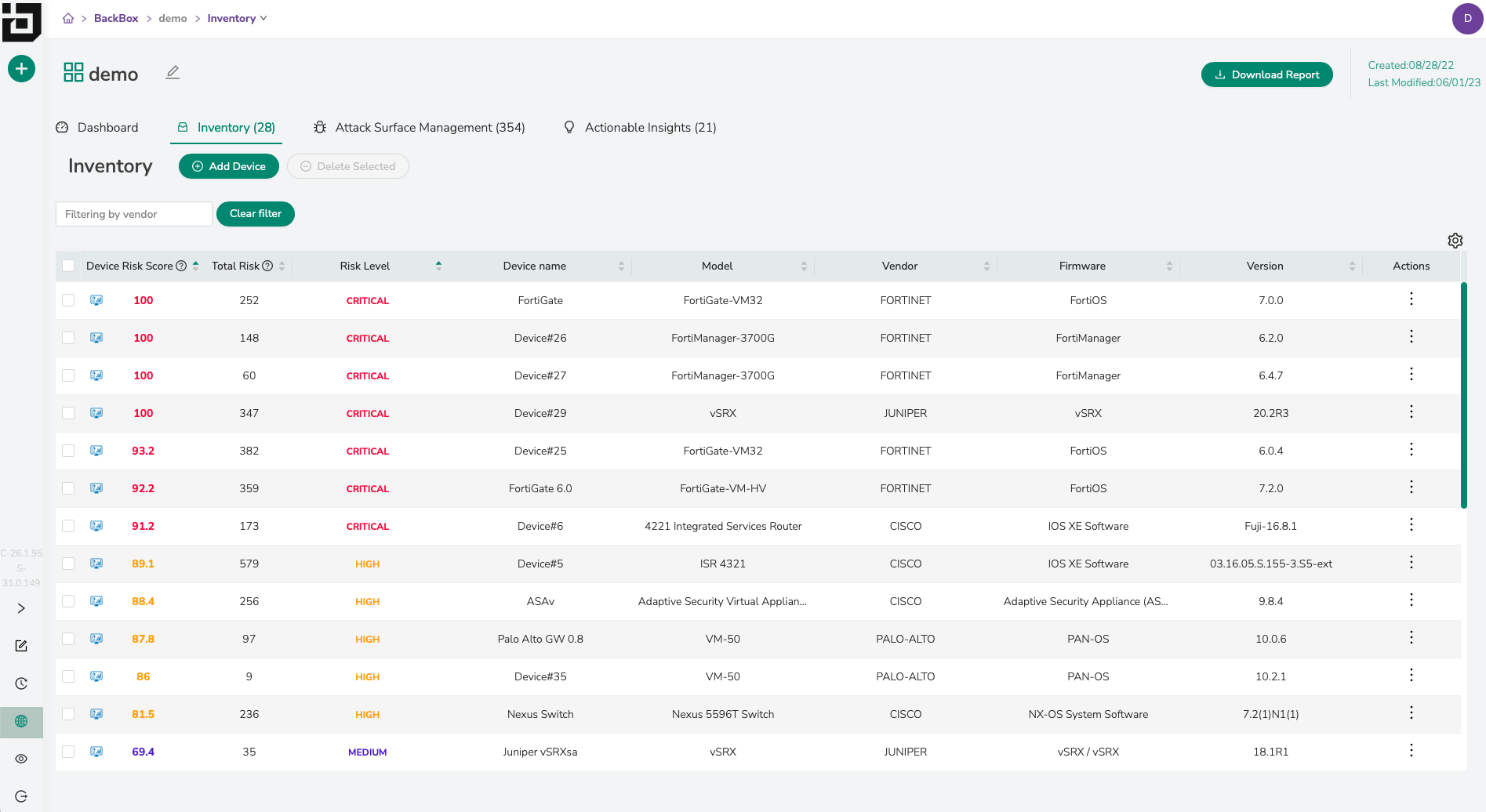
BackBox models your network’s configuration inventory and maps it against a threat intelligence feed using CVEs to assess each device’s threat level. To ensure the threat level is accurate, we compile the CVE information from three primary trusted sources: the National Vulnerability Database maintained by NIST, CISA’s KEV catalog, and advisories issued by our customers’ device vendors. - How do I prioritize vulnerabilities?
Using vulnerability mapping, each device is given a risk score based on the number of CVEs, its CVSS score, and other metadata. Organizations now have a punch list against actual inventory to decide which are irrelevant and which to address immediately or schedule for later. A standard security practice prioritizes any device with a score of 8 or greater to focus remediation or mitigation resources where the risk is greatest. - How do I communicate with other stakeholders to ensure vulnerabilities are patched promptly?
BackBox vulnerability intelligence provides network admins with the data they need to take a risk-based approach to communication. Gaining stakeholder buy-in with measurements and facts, rather than fear, is a much more effective and reliable way to get the investment needed for software updates. Metrics that show risk to the business also help make the case for replacing devices approaching end-of-life and no longer supported with vendor updates. - How do I deploy the patch quickly, efficiently, and without mistakes?
BackBox includes pre-built automations to make deploying updates easier, even for more complex update scenarios, including multi-step upgrades, upgrading high-availability pairs, innovative bulk changes, and incorporating backups and pre- and post-checks. In case of error, automatic rollback to a previous configuration, exception-based notifications, and reporting ensure no surprises. - How do I track vulnerabilities over time?
BackBox vulnerability intelligence closes the loop between identification and remediation. BackBox is a source of truth for network devices, maintaining a detailed inventory (including device manufacturer, type, model number, firmware and software version, and end-of-life). Vulnerability intelligence taps into this inventory so that your vulnerability analysis always reflects the current status of your devices. Given the volume and velocity of CVE information being released, it’s essential to have accurate inventory data to map against a constantly updated vulnerability and threat intelligence database so that you can best protect the enterprise. Closing the loop, your device inventory data is dynamically updated to the current OS version when updates are made.
We recognize that network admins have valid concerns about OS updates. By answering these five questions, we hope you will feel more confident that our vulnerability intelligence capabilities make it easy for you to take a more proactive approach to network security.
We’d love the opportunity to show you these capabilities in action. Schedule a 30-minute demo for an interactive tour of the BackBox platform.


