Fortinet Discloses 5 Critical and High Severity Bugs

In early March, Fortinet disclosed five new vulnerabilities. This sort of disclosure (from network companies in general) is not unusual. However, unusual or not, it presents a challenge to network administrators trying to keep their networks secure.
Here’s the fundamental challenge, from some BackBox sponsored research from last year:
92% say more network updates are needed than they can keep up with
Already overloaded, news of new vulnerabilities may not even break through the noise of a busy admin’s life, let alone be something they have time to address.
That’s the “why?” beyond BackBox Network Vulnerability Manager (NVM). NVM helps:
- Administrators easily keep TRACK of vulnerabilities
- Understand if they’re RELEVANT to their specific network inventory
- Determine the bigger context of CRITICALITY with a risk scoring of each vulnerability and device
- Quick and easily MITIGATE vulnerabilities
Tracking Vulnerabilities
BackBox delivers a vulnerability and threat feed containing CVE information along with additional context about the vulnerabilities relative to the devices affected. That’s a mouthful, but important. Many companies simply take the list of CVEs from the National Vulnerability Database and deliver that in some easily digestible format. That’s not enough!
BackBox gives you external context along with the CVEs. Is the vulnerability known to be exploited? What’s the impact of an exploit? How easy is it to be exploited? All of this information is important beyond a simple list of CVEs. Vulnerabilities can be viewed by device, seeing all the vulnerabilities on the device, or by vulnerability, and seeing all the devices impacted. In the following screenshot, you can see the list of CVEs with relevant devices for one highlighted.
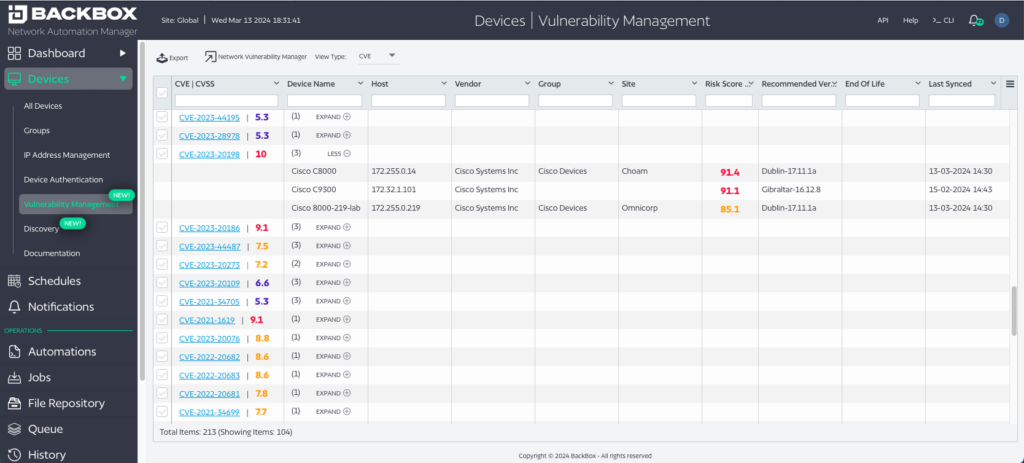
Relevant Vulnerabilities
Using search, network administrators can determine if a vulnerability is relevant. For example, back in October ’23 Cisco released CVEs on http server vulnerabilities. NVM users would quickly search all their Cisco configs to see if http server were set to determine if it were relevant. In fact, we quickly released an automation to mitigate this vulnerability by turning off http server and http secure-server, so network engineers who were able to turn those features off could do so quickly and easily at scale.
Vulnerabilities that aren’t relevant could be marked as such, with notes, so that they’re known not to be relevant and set aside. In fact, marking a vulnerability as mitigated/irrelevant takes that vulnerability out of the risk score measurement we’ll discuss next.
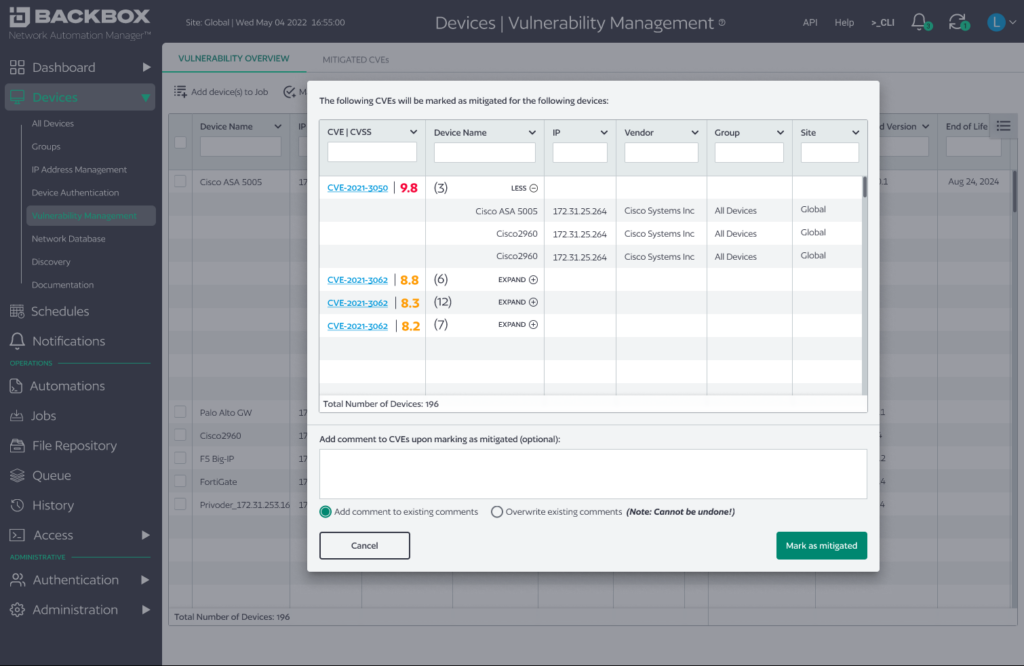
Vulnerability Criticality
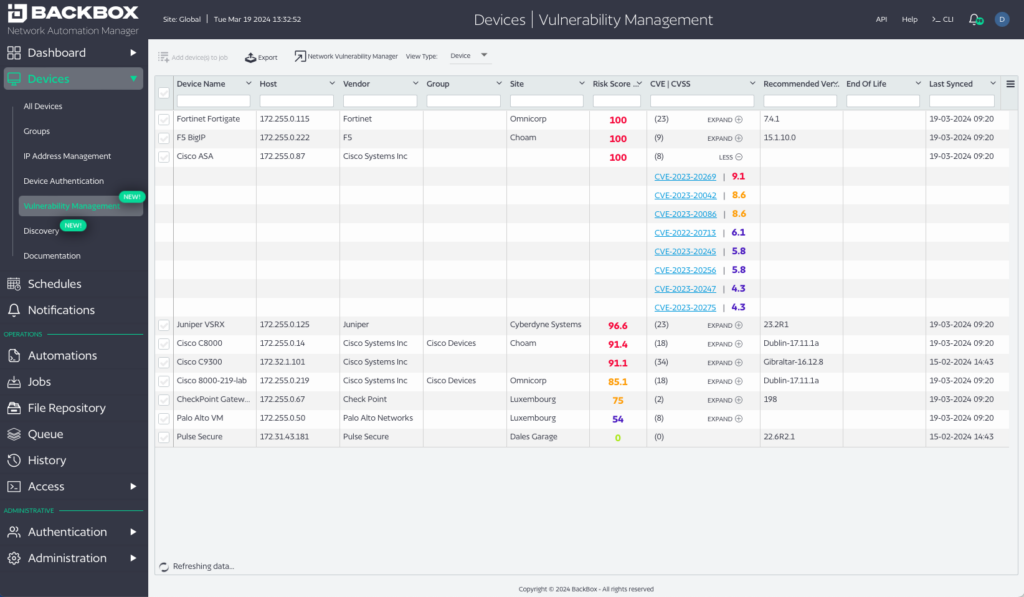
Again, it’s not only about a list of CVEs but understanding the context of vulnerabilities relative to the user’s network inventory. NVM does this by assigning a risk score to each CVE and device. This risk score reflects the impact of the vulnerability on the network by incorporating, for example, the number of CVEs on a device, how easily they’re exploited, whether they’re known to be exploited, the severity of the exploit, etc.
If we recap from above… NVM helps track vulnerabilities, determine which are relevant, and then of those relevant, helps understand the potential severity of the vulnerabilities. Using this information about severity (or criticality) engineers can prioritize remediation.
Mitigate Vulnerabilities
Only BackBox NVM ties together an understanding of CVEs relative to the exact inventory with the ability to take action and mitigate vulnerabilities. Of course, this is the most important thing! Understanding vulnerabilities is just an intermediate (and necessary) step towards remediation. Understanding on its own, like so many other solutions, is not enough.
Of course, as mentioned above, network engineers already have more than they can do even without dropping everything to patch vulnerabilities when they randomly pop-up without any concern for our existing workloads. NVM closes the loop between awareness and remediation with automation.
In the following image, you can see how a Fortinet Fortigate is being added to an update automation to eliminate vulnerabilities.
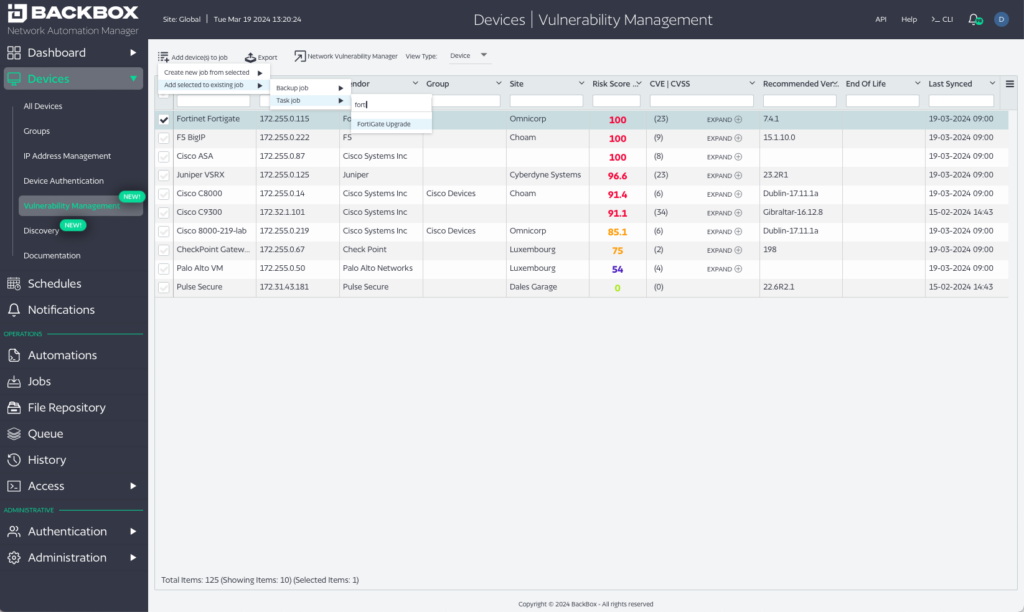
Conclusion
You can’t control the inputs – vulnerability notices from vendors – but you can control how you respond. Can you respond quickly? Can you quickly triage vulnerabilities to understand their severity and impact? Can you quickly and easily mitigate vulnerabilities? These are the questions you need to ask yourself otherwise you’re doing your organization a disservice. No matter how busy we all are, we need to keep our networks safe.
To learn more check out our Network Vulnerability Manager Solution Brief.


