Closed-Loop Vulnerability Remediation with BackBox
Using dynamic inventory together with risk data and scoring to help administrators prioritize and perform device OS updates with the greatest impact on network security.
Overview
As cyber-attacks leveraging unpatched devices become a common practice, an effort-saving comprehensive network security management platform is a must, empowering businesses to proactively identify vulnerabilities and strengthen their defenses against cyber threats.
Through 2026, more than 60% of threat detection, investigation and response (TDIR) capabilities will leverage exposure management data to validate and prioritize detected threats, up from less than 5% today.” Gartner 12/22
This presents a challenge for network and security device administrators.
Vulnerability patching for endpoints and compute systems is easy compared to patching network and security devices. Updating devices like firewalls, IDSs, IPSs, routers, switches, and WAPs to patch CVEs is much more complicated, as each device impacts the entire network operations and security infrastructure. The BackBox Network Automation Platform, working together with our Network Vulnerability Manager is designed to optimize the work invested in OS Updates in a way that maximizes the security impact on the network.
NIST lists over 2,500 CVEs per month. That’s a lot of “out of context security information” for network administrators to consume. CVEs also serve, in part, as a roadmap for attackers to target network vulnerabilities. It’s important to understand how CVEs pertain to your specific network inventory, taking the risk to your organization from the abstract to the specific.
The challenge is that permanently addressing the vulnerabilities disclosed in the CVEs requires an OS update or patch to the network devices in question. These updates are often complicated and time consuming, requiring after-hours work, sometimes with an impact on the business.
This results in OS updates and vulnerability patches being delayed and deprioritized even though “unpatched software is a top three access route for hackers and patching remains the single most important thing you can do to secure your technology.” 1
Fortunately, there’s now a better way for network operations teams and service providers of all sizes to protect networks while reducing the intensity of manual work these software updates entail.
1 https://thestack.technology/analysis-of-cves-in-2022-software-vulnerabilities-cwes-most-dangerous/
CLOSED-LOOP VULNERABILITY REMEDIATION
- Dynamic Inventory. With BackBox there’s no guessing about your inventory. You want to make sure you have a complete and current view of your network and security devices. Often, collecting inventory information is an error-prone, manual process completed as part of provisioning new devices or updating existing ones. With BackBox collecting your inventory is simple, automatic, and you can trust that the inventory information passed into a vulnerability risk scoring engine is complete and accurate.
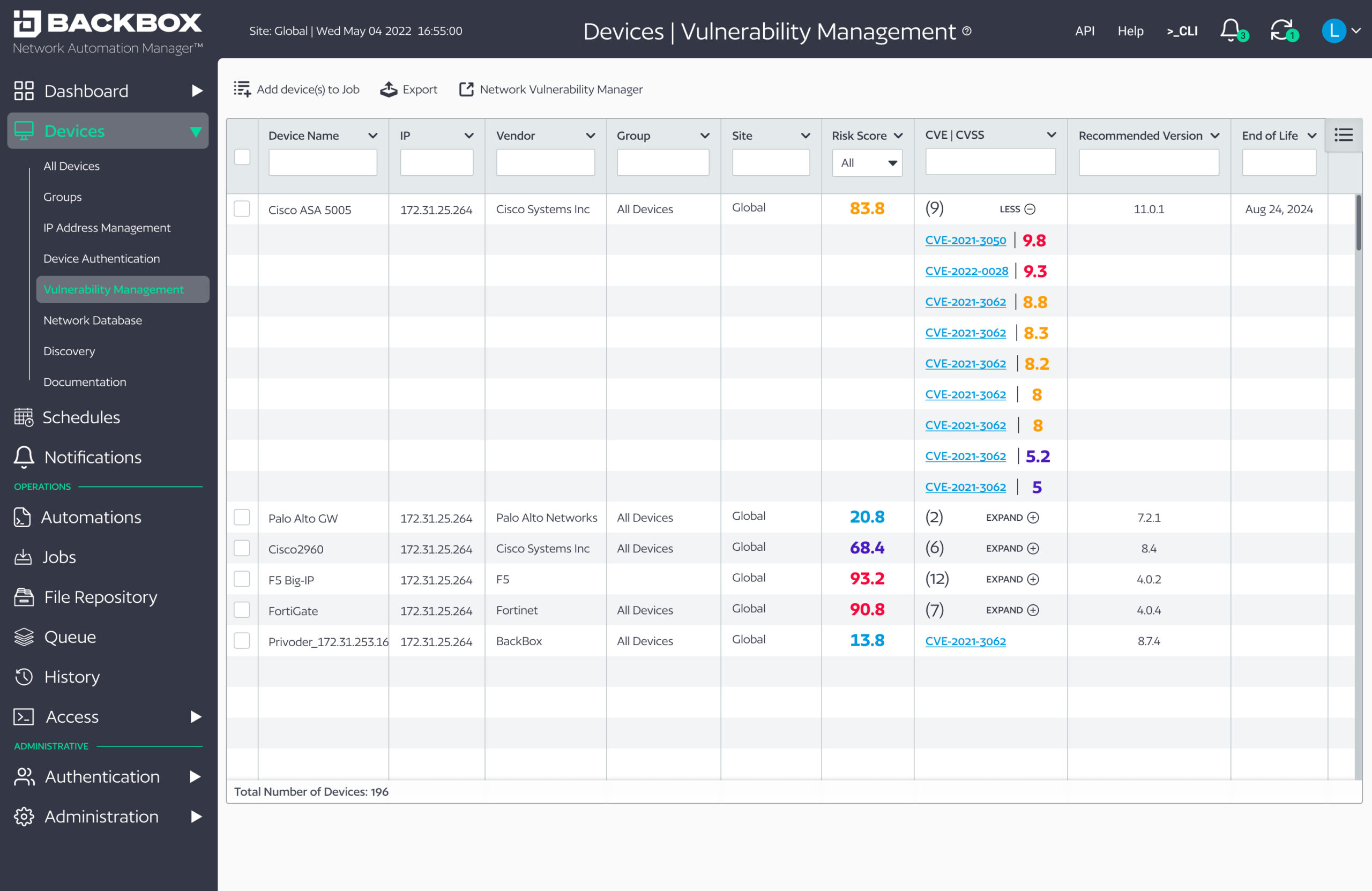
- Risk Scoring and Analytics. The BackBox Network Vulnerability Manager risk scoring engine reviews vulnerabilities impacting the organization and provides attack surface score and risk metrics for every connected device on the network. It understands and presents contextual risk across all devices and networks for a complete view of network vulnerabilities and risk exposure.The risk score integrates CVSS scores along with the number of CVEs on the device, whether or not a CVE is under active exploit, and if the device being scored is internet facing.
- CVE Mitigation. Administrators can search device configuration files for specific vulnerable configurations to determine the relevance of any given CVE. If a vulnerability is found, using automation it can be mitigated, and once mitigated it’s removed from the risk score. However, some CVEs will be determined to be irrelevant to the device. In that case, administrators can make the CVE as non-applicable to the device, causing the risk score to recalculate and present an accurate view on the vulnerability state of the device. These non-applicable CVEs, called “mitigated” in the product, can be managed in their own interface so that if they become relevant at some point later in the future they can be re-added into the vulnerability manager.
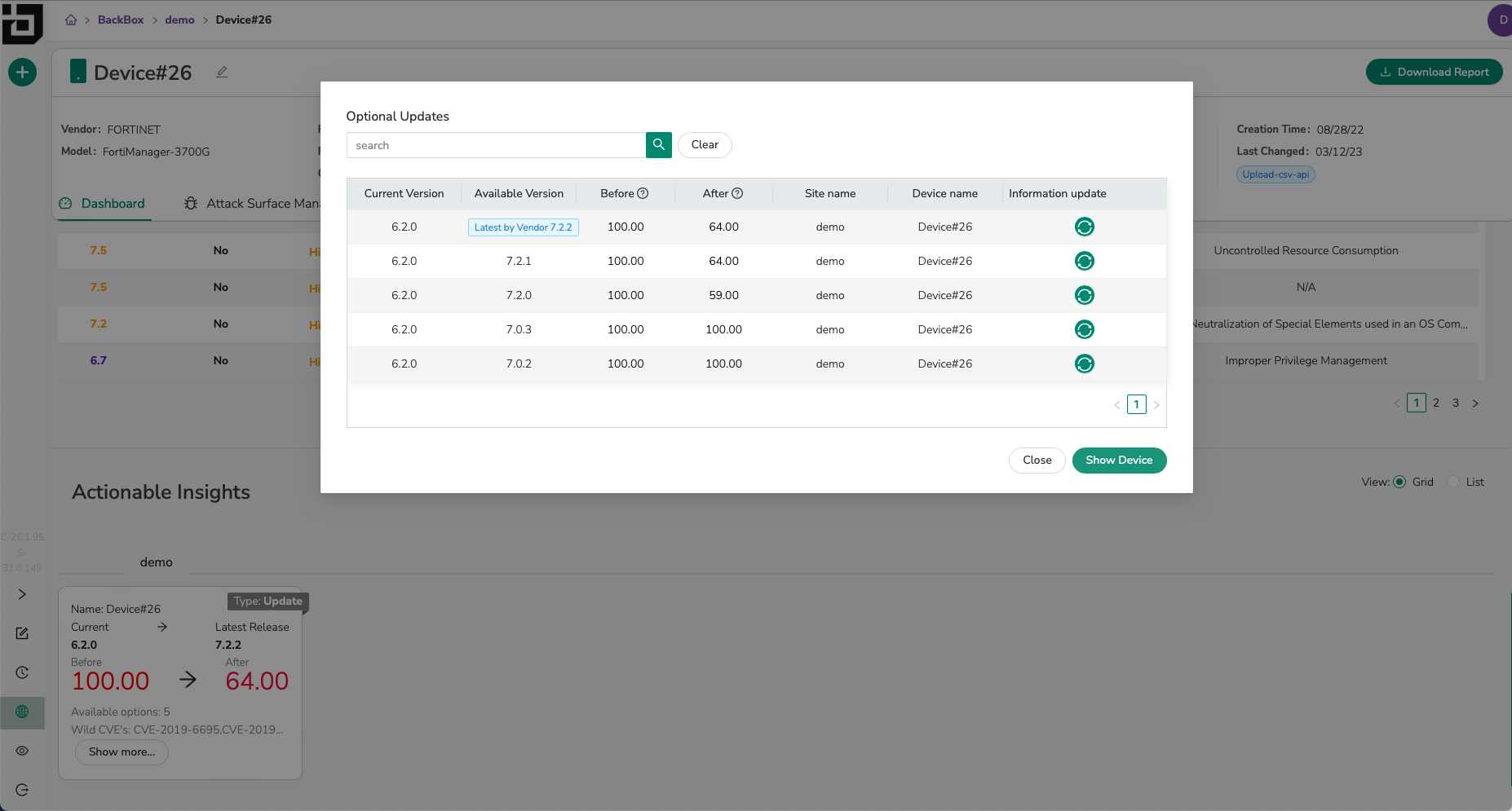
- Remediation Prioritized by Risk Analysis. BackBox takes the complexity out of the patching process while giving administrators risk analysis data to prioritize updates. This data helps create consensus and provides a complete picture around the priority of vulnerability patching, while the pre-built automations make deploying updates easier than ever before. Network Vulnerability Manager even provides insight into step-upgrades, enabling organizations to easily understand how their security posture improves by updating, but not to the most recent version.
Most network engineers would agree that updating an OS for the sake of it is an administrative exercise, but that patching vulnerabilities is critical. Should CVEs expose vulnerabilities there are important steps to take immediately, followed by the software update which is a permanent fix.
Let’s explore the process of vulnerability patching in a little more detail.
Without BackBox
There are five elements to patching vulnerabilities:
Understand your inventory and exposures
Determine the update priorities
Remediate with temporary configuration fixes
Remediate permanently with OS updates
Remove temporary configuration fixes
We hear from many of our customers that this end-to-end update cycle is a manual process. Even when inventory is kept in a central system, there’s a lack of confidence that it is complete and up-to-date for an important task like vulnerability patching due to shortcomings in the discovery process.
Similarly, the inventory system is not a “working system.” Inventory needs to be exported somewhere (like a spreadsheet or database) to verify it and perhaps manipulate it, for example, ordering vulnerability patches by priority relative to business need. Additionally, once the inventory is out of the inventory system, it should be assumed to be out of date with any adds, moves, or changes that occur after the export.
Once visibility into inventory is available, a similar exercise needs to happen with CVEs.
CVEs, if they’re tracked at all, are tracked manually in a spreadsheet or a database, with some limited ordering based on priority and associated with the equipment in the inventory. Additional information can be correlated manually from other sources to enrich that presented in the CVE. It’s a lot of manual effort.
This can result in ambiguity and blind spots. For example, how does my security posture improve if I update to a newer version, but not the latest, a common practice. Or, of the critical vulnerabilities my network is exposed to, which ones are currently being exploited in the wild? You might prioritize those vulnerabilities with known exploits, if that exploit information were presented in the context of the rest of the security scoring.
Temporary configuration changes are easy enough to make with the usual processes at the organization, but software updates remain highly disruptive. Additionally, temporary configuration changes have a nasty habit of becoming permanent, simply due to a lack of systems to track which devices have been temporarily patched, and then updated.
Lacking a security score and hard data on the impact of potential protection updates, they’re moved to after-hours administrative work driven by a vague notion that being on the latest version is better. And, without automation closing the loop between inventory and the vulnerability patch, the effort is time consuming, error prone, and leaves a big time-gap between known vulnerability and patched vulnerability that can be maliciously exploited.
With BackBox Network Vulnerability Manager
Devices are discovered through an automated process. Once discovered, an inventory is collected which is used later in the flow to map against vulnerabilities and CVEs.
After the initial discovery and inventory, administrators continue to gain daily inventory information directly from the network itself through a discovery-automation rather than having to depend on manually tracking adds, moves, and changes. Having a daily inventory means that information about the network is always up to date.
Administrators use risk and vulnerability scoring to prioritize OS updates and configuration changes that help protect the organization.
Administrators can also view their vulnerabilities by CVE to make it easier to manage to a particular vulnerability that they know requires attention.
Sometimes CVEs are determined to be irrelevant to a particular device (or group of devices). In the CVE detail, administrators can search through device configurations to look for the configuration elements being exploited. If they’re not present, these CVEs can be marked ‘mitigated’ so they are removed from the risk scoring giving network teams a more accurate view on their vulnerability state. CVEs can be marked ‘mitigated’ on a per device basis allowing for a lot of flexibility in how vulnerabilities are managed.
Like the network inventory, the CVE, vulnerability, and risk data that informs the analysis is also updated daily. The result being that both inventory and vulnerability/risk information is updated and correlated daily, giving administrators a current view on their network exposure to cyberthreats.
Administrators have a view on their specific environment, so that if a latest release has a bug affecting their deployment, risk-adjusted scenarios can be examined to determine the optimal update path.
Administrators can update devices in the most efficient way possible, whether updates require multi-step updates or high-availability awareness.
Conclusion
[Vulnerability] patching remains the single most important thing you can do to secure your technology and is why applying patches is often described as ‘doing the basics’.” 2 (UK National Cyber Security Center; Jul 10, 2019)
Vulnerability patching is hard. It’s time-consuming, manual work often done after-hours. While BackBox has always made it easier and faster to complete updates, they were still done without insight into vulnerability severity or the actual risk to the organization, until now.
With BackBox Network Vulnerability Manager, networks can be kept more secure, with OS updates prioritized by risk and vulnerability data.
Administrators can act on known inventory and be certain they have complete network visibility. Inventory is correlated with up-to-date data on CVEs and known risks, giving administrators a current view on their network exposure to the latest cyberthreats. And, as always, updates are done in the most efficient way possible with support for over 180 vendors in the built-in Automation Library.
2 https://www.ncsc.gov.uk/blog-post/the-problems-with-patching
About BackBox
Backbox is a Network and Security Device Automation Platform that supports
over 180 vendors, with thousands of pre-built automations and a scriptingfree
way to build new ones. Enterprises and service providers worldwide trust
BackBox to automate and audit anything an admin could do manually, with reliable
automations that are flexible, scalable and contextually aware. From backups
and OS updates to configuration compliance, BackBox gives you confidence
that your automations will deliver the expected outcome every time.
To learn more or download an evaluation copy, visit backbox.com
![NVM Mitigation Screenshot 1[20] NVM Mitigation Screenshot 1[20]](https://backbox.com/wp-content/uploads/NVM-Mitigation-Screenshot-120-1.png)
![NVM Mitigation Screenshot 2[83] NVM Mitigation Screenshot 2[83]](https://backbox.com/wp-content/uploads/NVM-Mitigation-Screenshot-283.png)