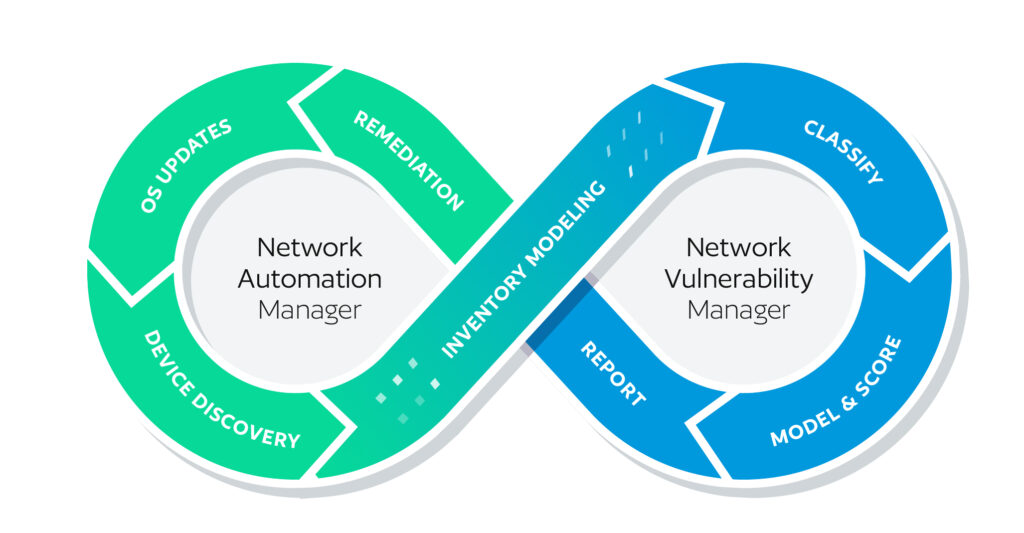
The Vulnerability Lifecycle
BackBox NVM helps manage the entire vulnerability lifecycle, with differentiated capabilities along the way. The purpose of this post is to highlight the lifecycle and BackBox unique differentiation. It’s inspired by this image of how a CVE gets created: There are three steps in the vulnerability lifecycle: Assessment Application Action Assessment The two main questions […]